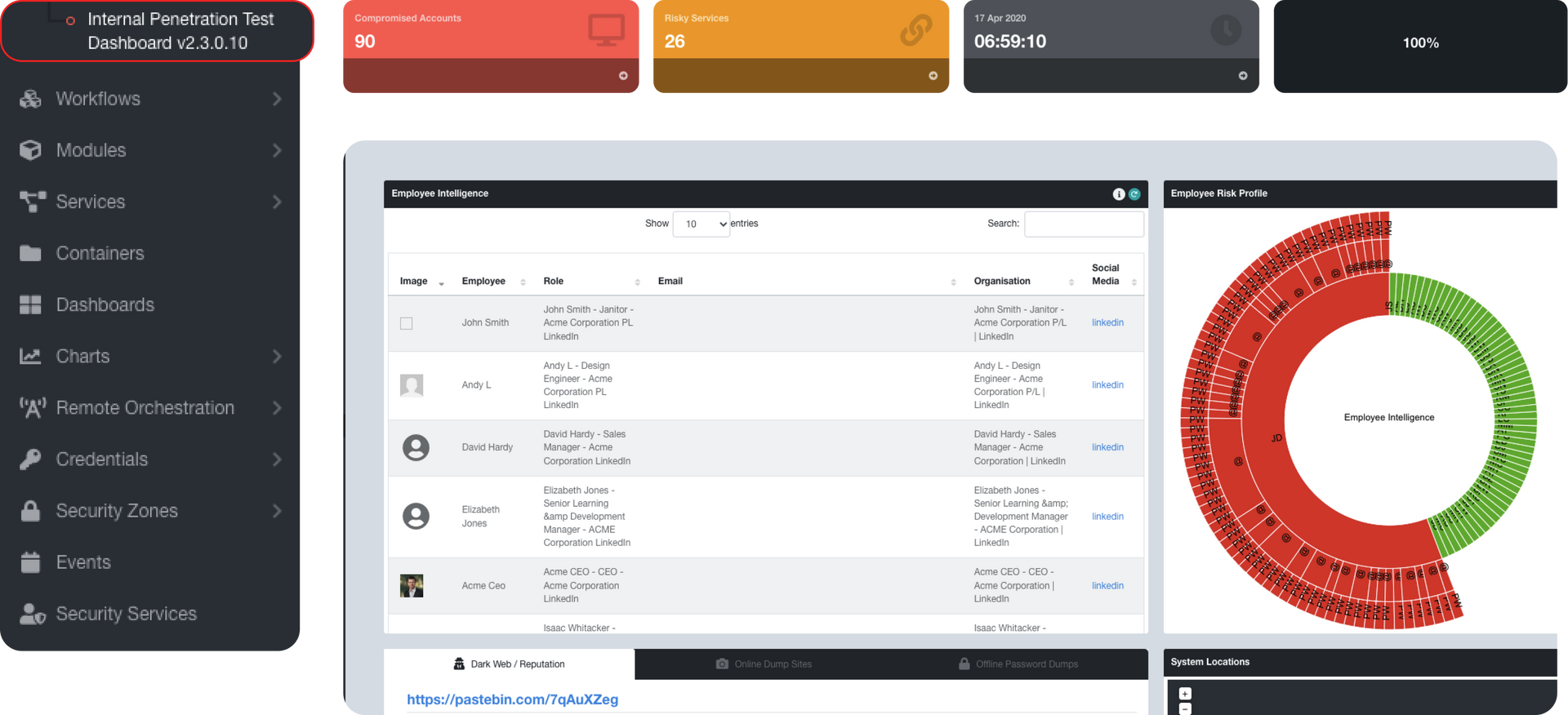
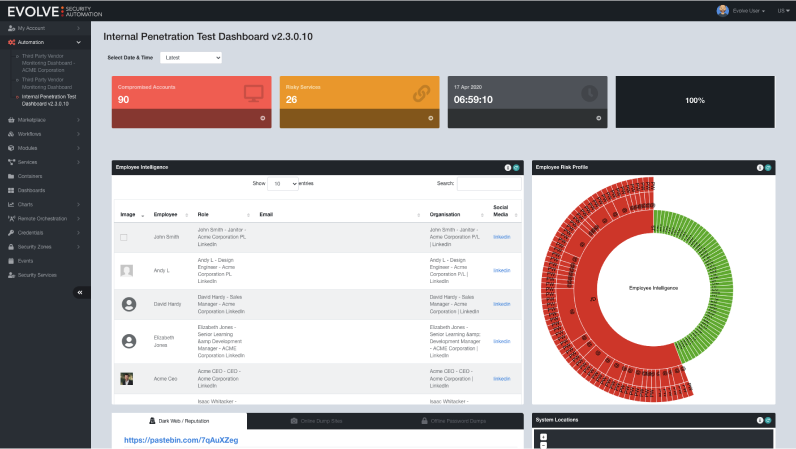
Run regular automated application security tests to stay on top of the latest vulnerabilities and manage critical risks

Secure DevOps Orchestration.
EvolveAST helps organizations orchestrate and automate the integration of application security testing into your DevOps pipelines
Integrating Security into DevOps
No matter where you are on your Startup, SMB or Enterprise journey, integrating automated security testing into your DevOps pipeline is challenging and can takes months of planning and incur significant project costs.

Empower your Development Team
Evolve empowers your development teams to efficiently and effectively reduce risk through the automated integration of application security testing into their standard Business as Usual (BAU) processes and technologies. This helps developers gain faster access to application-layer vulnerabilities for every code deployment, preventing vulnerabilities from progressing through to production applications.

Continous Security Validation
Running regular automated and repeatable application security tests help you stay on top of the latest vulnerabilities and manage critical risks throughout the year. Verify remediation actions immediately to ensure their effectiveness and identify any new avenues of attacks.
Key Features
- JUnit Results Support
- OS Command Injection
- Server-Side Code Injection
- Server Side Include
- SQL and NOSQL Injection
- Path Traversal
- Error Handling and Information Disclosure
- Directory Browsing
- Insecure Session Management
- Remote File Inclusion
Selected to conduct and manage penetration testing examinations for the Australian Government, our team members not only hold positions on the Board of Directors of CREST Australia and New Zealand, but also lead the CREST Technical Team.

With extensive experience in the longest running training course at Black Hat USA and a position on the Black Hat Asia Review Board, our trainers are renowned for their expertise in the most recent threats and the cutting-edge techniques to combat them.

Threat Intelligence contributes to the development of global security methodologies, standards, and libraries that are incorporated into industry-specific security regulations of the Open Web Application Security Project (OWASP).

The Team Behind Evolve
Ready to Get Started?
Is your organization looking for a complete cyber security solution? With our products and services, your team can take a propositive security posture. Let’s chat.