In this blog post, we will explore the differences between Antivirus (AV), Endpoint Detection and Response (EDR), and Extended Detection and Response (XDR) solutions, helping you make an informed decision for your organization's endpoint security needs.
Understanding Antivirus, EDR, and XDR
Endpoint security solutions have evolved from traditional Antivirus (AV) software to more advanced solutions like EDR and XDR. Here’s how each of them works:
- Antivirus (AV) Software: AV software identifies and blocks known malware based on signature-based detection. Its primary goal is to prevent malware infections. While AV software is still essential, it has limitations in detecting unknown threats and providing incident response capabilities.
- Endpoint Detection and Response (EDR) Solutions: EDR solutions take endpoint security to the next level by recording and storing endpoint behaviors, detecting suspicious activity, and providing contextual information, containment, investigation, and remediation guidance. EDR solutions focus on detecting security incidents, containing them, and providing remediation suggestions.
- Extended Detection and Response (XDR) Solutions: XDR solutions build upon EDR capabilities by integrating threat intelligence and telemetry data from multiple sources, providing contextualization and correlation of security alerts. XDR solutions offer security incident detection and automated response capabilities, making them ideal for organizations with smaller security teams.
In the upcoming sections, we'll dissect the unique strengths and weaknesses of each solution, helping you choose the best fit for your organization's distinct endpoint security needs.
EDR and XDR: Marketing Hype or Game-Changers?
As the attack surface expands and endpoint threats evolve, the quest for a suitable security solutions intensifies. While some argue that traditional antivirus software remains sufficient, others advocate for advanced technologies like EDR (Endpoint Detection and Response) and XDR (Extended Detection and Response). But are these solutions truly game-changers, or just marketing hype designed to drive sales?
In this section, we’re breaking down the inner workings of EDR and XDR, to help you determine if they're essential for your security arsenal or just a fancy repackaging of existing capabilities.
Unpacking the Evolution of EDR and XDR
As the threat landscape continues to evolve, Endpoint Detection and Response (EDR) and Extended Detection and Response (XDR) have emerged as the next generation of security solutions. But are they merely rebranded versions of traditional antivirus products or significant improvements? A closer examination reveals that while some vendors have indeed rebranded their AV offerings with added response capabilities, true EDR and XDR solutions represent a paradigm shift in threat detection and response.
AV solutions, which rely on signature-based detection, are limited to preventing known threats and struggle to keep up with the evolving threat landscape. In contrast, EDR solutions examine behavior and detect potential threats based on behavioral analysis, providing continuous monitoring, real-time threat detection, and incident response. EDR goes beyond prevention by being proactive, offering security teams valuable intelligence through telemetry analysis across the endpoint landscape. This enables organizations to identify patterns and anomalies, including APTs, zero-day, and N-day attacks, and perform threat hunting activities to proactively defend against new threats.
XDR takes this further by correlating data from multiple sources, including EDR, SIEM, NDR, and threat hunting, to provide a unified view of threats. XDR's capabilities extend to telemetry, analytics, detection, response, threat hunting, investigation, cloud protection, and more. It reduces sprawl and operational costs by providing a single place to manage all risks, also incorporating information from Attack Surface Management and Vulnerability Management.
Real-World Insights: SOC Team Perspectives on EDR and XDR Effectiveness and Challenges
Security Operations Center (SOC) teams are on the frontlines of threat detection and response, making them uniquely qualified to assess the effectiveness and challenges of EDR and XDR solutions. We spoke to Mark Alvarez, Incident Responder and Senior SOC engineer at Threat Intelligence, to gain insight into the effectiveness and challenges of EDR and XDR solutions. "All three - AV, EDR, and XDR - are designed to protect against malicious software," Mark explained. "But traditional antiviruses were limited in their capabilities. They'd clean up malware after infection, but couldn't stop remote execution components or lateral movement."
Mark noted that many antivirus vendors have rebranded their products as EDR solutions, adding response capabilities to their offerings. "XDR, on the other hand, evolved from the SIEM concept," he said. "It aggregates data from various systems, including cloud services, and generates alerts. It's like a SIEM with extended coverage and response capabilities."
When discussing the differences between EDR and XDR, Mark emphasized that "EDR is specific to endpoints and doesn't analyze network traffic. XDR, however, provides more visibility by bundling multiple log sources, including SOC data."
This increased visibility comes with a challenge, though: managing the sheer volume of alerts. "That's why XDR is often better suited as a managed service, with a human component to analyze and triage alerts," Mark advised.
In terms of deployment, Mark recommended that "for personal computers, AV might suffice, but in corporate settings, EDR or XDR is a must." He also emphasized that while we can live without an antivirusl, a solution that stops malware from harming computers is crucial. "XDR's focus on aggregating log sources makes it a more comprehensive solution," Mark concluded.
A Guide to the Right Solution
So what’s the best solution for you? With various options available, it's essential to understand that this choice heavily depends on what you're trying to achieve. However, at a minumum, your organization must be able to detect and respond to threats. Here are some key factors to consider during evaluation:
Cost and ROI
The potential return on investment (ROI) after getting an XDR is often cause for concern for businesses. And for small-medium businesses, budget constraints are a harsh reality.
When evaluating solutions consider the following:
- Total cost of ownership, including licensing fees, implementation costs, and ongoing maintenance expenses
- Potential return on investment (ROI) by considering the potential costs of a data breach or cyber attack
We recommend exploring budget-friendly options that offer managed XDR capabilities at a lower price point. While a budget-friendly XDR solution might not have all the features, capabilities, or coverage of a more expensive XDR solution, it's still a better option than nothing, and it's more affordable.
Resource Requirements
Evaluate the resources needed to effectively manage, optimize, and utilize these security tools. Consider the following factors:
- Expertise: Do you have the necessary in-house skills and knowledge to handle the solution, or will you need to hire additional personnel or train existing staff?
- Personnel: How many people will be required to manage and monitor the solution, and what are the associated costs?
- Infrastructure: What are the hardware, software, and network requirements to support the solution, and are there any potential compatibility issues?
If you find that your organization lacks the necessary resources, consider outsourcing your security to a managed security service provider (MSSP). This can be a more viable and cost-effective option, allowing you to tap into expertise and resources that might otherwise be out of reach.
Sources of Risk
When evaluating cybersecurity solutions, it's essential to consider the sources of risk to your organization. If you're facing multiple, evolving threats, antivirus software may be insufficient, making Endpoint Detection and Response (EDR) or Extended Detection and Response (XDR) a better choice. Additionally, if your organization has a complex IT environment, XDR provides more comprehensive coverage and visibility, helping you stay on top of potential threats.
Regulatory Requirements
It's crucial to ensure that the chosen solution meets applicable regulatory requirements. This includes continuous monitoring for compliance requirements, which can be a challenge for many organizations. Furthermore, some
cyber insurance providers now require XDR solutions, making it essential to factor this into your decision-making process.
Capabilities Checklist and Conclusion
As we've explored in this post, the landscape of endpoint security has evolved significantly, with various solutions emerging to address the growing threats. Let's recap the key points:
- Antivirus (AV) focuses on signature-based detection, with limited scope and no cross-platform integration.
- Endpoint Protection Platform (EPP) offers more comprehensive endpoint security, but is generally limited to the endpoint layer.
- Endpoint Detection and Response (EDR) detects and responds to threats at the endpoint level, with advanced capabilities, but primarily centered on endpoint protection.
- XDR extends detection and response capabilities beyond endpoints to include networks, servers, cloud, and other security layers, providing a holistic and integrated approach to threat management.
Schedule a consultation with one of our experts today!
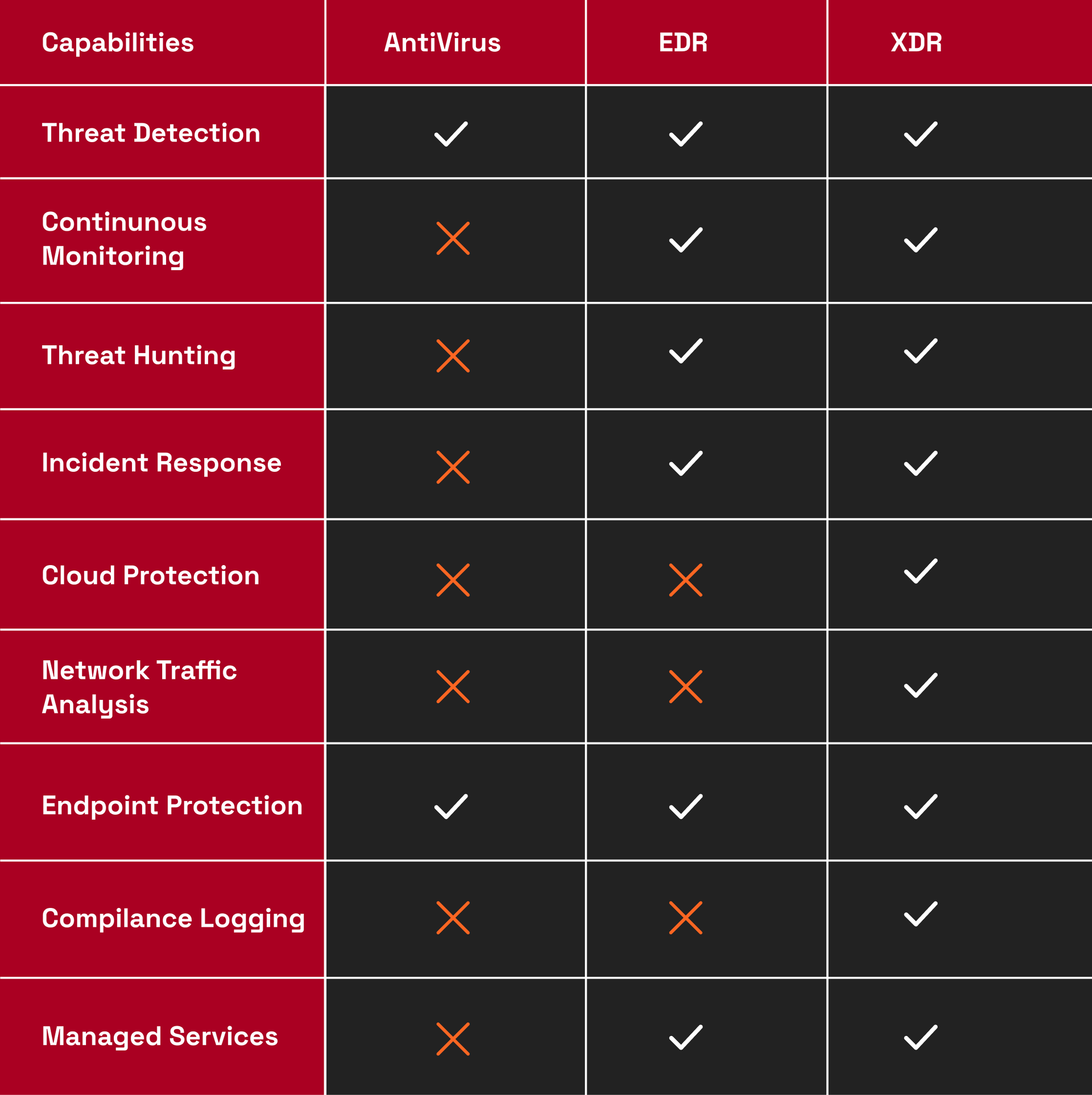
Note that in EDR solutions features such as Threat Hunting and Incident Response, focus on endpoint-related investigations, while XDR usually covers a broader spectrum, making it a more comprehensive solution.
XDR stands out for its benefits, including:
- Holistic Threat Detection: identifying threats that might be missed by isolated security solutions
- Improved Efficiency: centralizing threat detection and response, reducing the burden on security teams
- Faster Response: automated and coordinated responses across multiple security layers for quicker threat containment and mitigation
- Cross-Platform Integration: providing a unified view and streamlined security management across multiple platforms and security layers

Detect Hidden Threats with EvolveXDR
EvolveXDR offers three key benefits to transform your security posture:
- Consolidate and streamline security operations with our automated XDR solution, reducing manual effort and complexity.
- Detect and respond to threats more effectively with MITRE ATT&CK mapped threats and advanced security capabilities that cover your entire attack surface.
- Scale your security operations with ease, deploying unlimited agents at no extra cost to cover all your assets and protect your organization from evolving threats.
See How Our Automated XDR Solution Can Enhance Your Threat Detection >
Book a Free Demo.






