Services
Incident Response Services
Get fast containment, digital forensic investigation, and expert remediation assistance to stop security events from intensifying and spreading.
Navigate legal challenges for reduced revenue loss and fines.
24/7 Support and
Guidance
Deep Forensic Investigations
Incident Response Remediation and Reporting
Proactive Legal-Cyber Partnership for Risk Mitigation
Our Distinctive Method for Managing Data Breaches
Enhance Your Incident Response Team: Through every phase of incident response, our team partners closely with your in-house security professionals. Collectively, we enhance your incident response capabilities, bolstering your security stance while unveiling hidden malicious activities. With our support, you'll approach outcomes with confidence, never navigating these challenges alone.
Post-Incident Legal-Cyber Support: Our vigilance extends beyond containment, offering a 30-day monitoring option to prevent threats from resurfacing. Should you require more, we provide ongoing monitoring that seamlessly aligns with your incident response plan. Our commitment is steadfast; we're dedicated to restoring operational fluidity and upholding digital security. Moreover, our alignment with legal experts ensures focused damage control, further safeguarding your organization's reputation and stability.
Combining Expertise and Tools for Rapid Response:
With our deeply experienced security team and the advanced capabilities of EvolveIR, we offer a genuine and swift incident response solution. In less than an hour, our team can confirm breach, identify the entry point, check for leaked credentials analysis, detects malicious domains and compromised systems, automates forensic evidence gathering, start isolation to secure environment and implement post-threat monitoring.
"Thanks to the exceptional Incident Response Management at Threat Intelligence, we were able to quickly address a major security breach of our network and mitigate the impact.
The team was able to identify the root cause of the breach, check for stolen privileged accounts, and company data that might have been exposed. They were also able to centralize and coordinate all of the necessary cyber security telemetry and response data that was relevant to the breach. The team's efforts were critical in helping us to quickly resolve this issue and protect our network.
We highly recommend TI's Incident Response team to any organization seeking top-notch cybersecurity expertise, quick and effective incident response, and a reliable partner in cybersecurity."
CISO
Healthcare
Enterprise

Board Tabletop Exercises: Strengthen Your Incident Response Plan & Enhance Your Preparedness
Elevate your incident response strategy with our Board Tabletop Exercises. Tailored to your business, these simulations empower your leadership to make informed decisions in real-world crisis scenarios. Strengthen your readiness today. Most common Table Top Exercise Scenarios:
- Stolen or Compromised Credentials
- Cloud Misconfigurations
- Ransomware Containment
- Insider Threat
- Data Breaches and Leaks
- Third-Party Data Breach
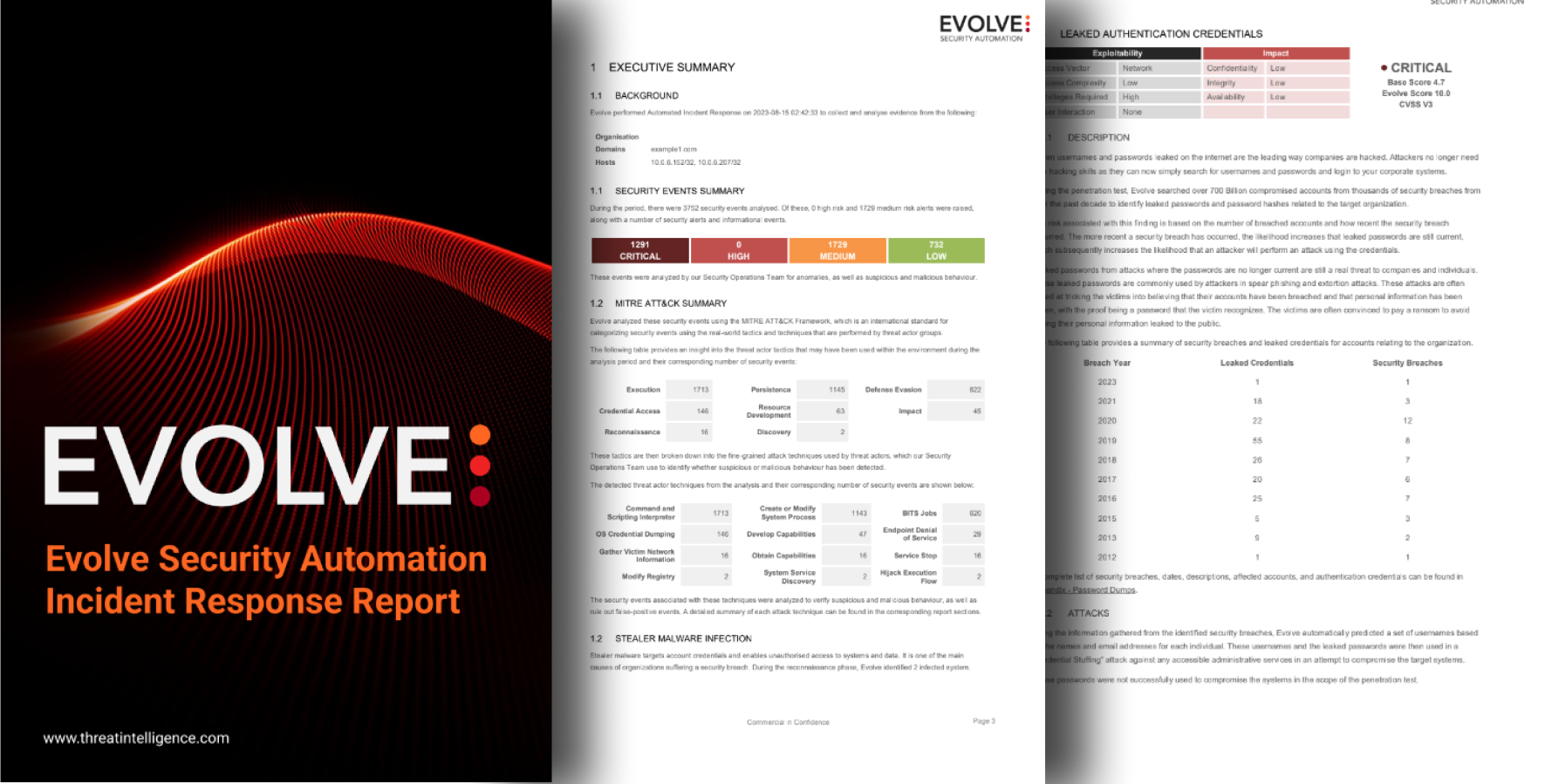
Download the sample report to see how EvolveIR, automated incident response tool, can quickly detect and respond to security threats, saving time and reducing manual effort.
Threat Intelligence: Defending Businesses from Major Security Breaches
Unique Expertise in Security Breach Management: Every month, our specialist team manages major security breach investigations and multi-million-dollar ransom and extortion campaigns for local and global organisations. These threats impact businesses across the spectrum, from startups to multinational corporations.
Proven Track Record: Proudly, our company has provided crucial support during significant data breaches, including the Medibank 2022 and the Latitude 2023 incidents. Our experience speaks volumes about our capability and dedication to safeguarding businesses' digital landscapes.
Comprehensive Protection for Australian Business: The scale of major security breaches knows no boundaries, posing risks to businesses of all sizes in our country. Our adept team is equipped to handle the challenges faced by small, medium, as well as established enterprises.

Selected to conduct and manage penetration testing examinations for the Australian Government, our team members not only hold positions on the Board of Directors of CREST Australia and New Zealand, but also lead the CREST Technical Team.

With extensive experience in the longest running training course at Black Hat USA and a position on the Black Hat Asia Review Board, our trainers are renowned for their expertise in the most recent threats and the cutting-edge techniques to combat them.

Threat Intelligence contributes to the development of global security methodologies, standards, and libraries that are incorporated into industry-specific security regulations of the Open Web Application Security Project (OWASP).

The Team Behind Evolve
Ready to Get Started?
Is your organization looking for a complete cyber security solution? With our products and services, your team can take a propositive security posture. Let’s chat.
