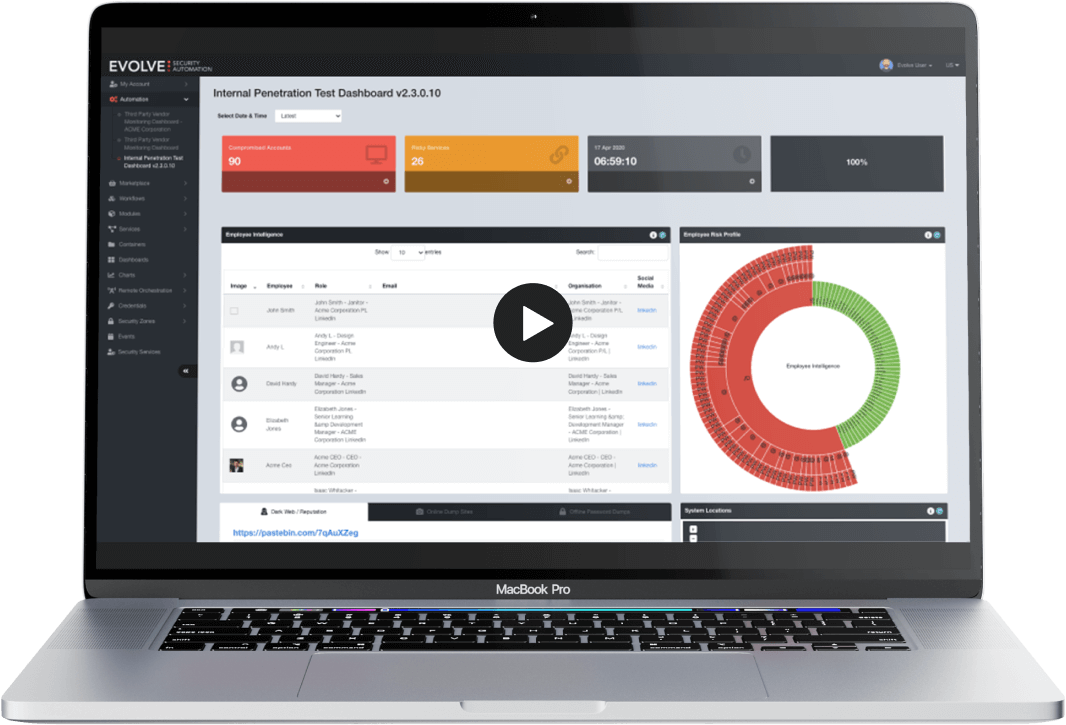
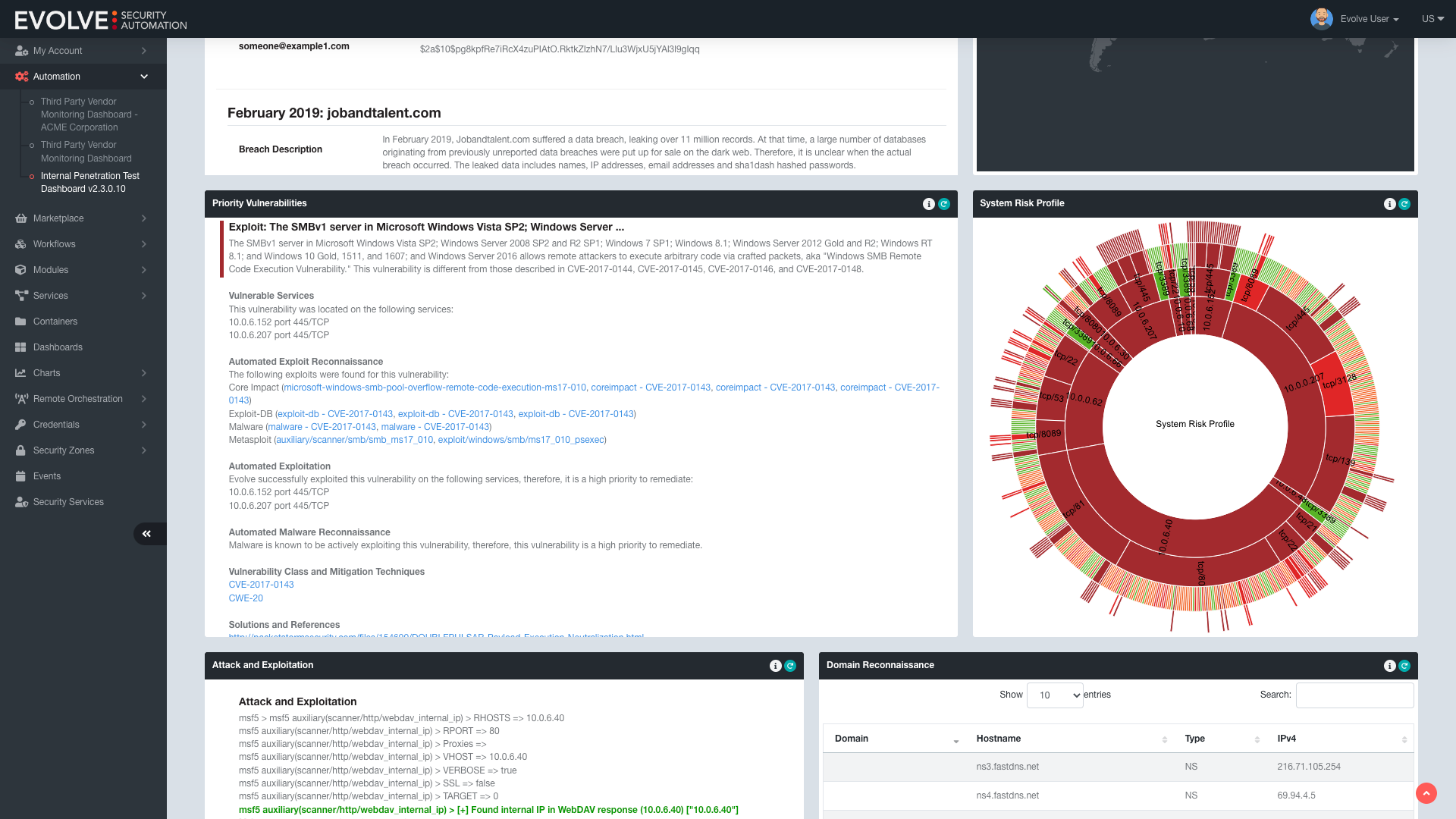
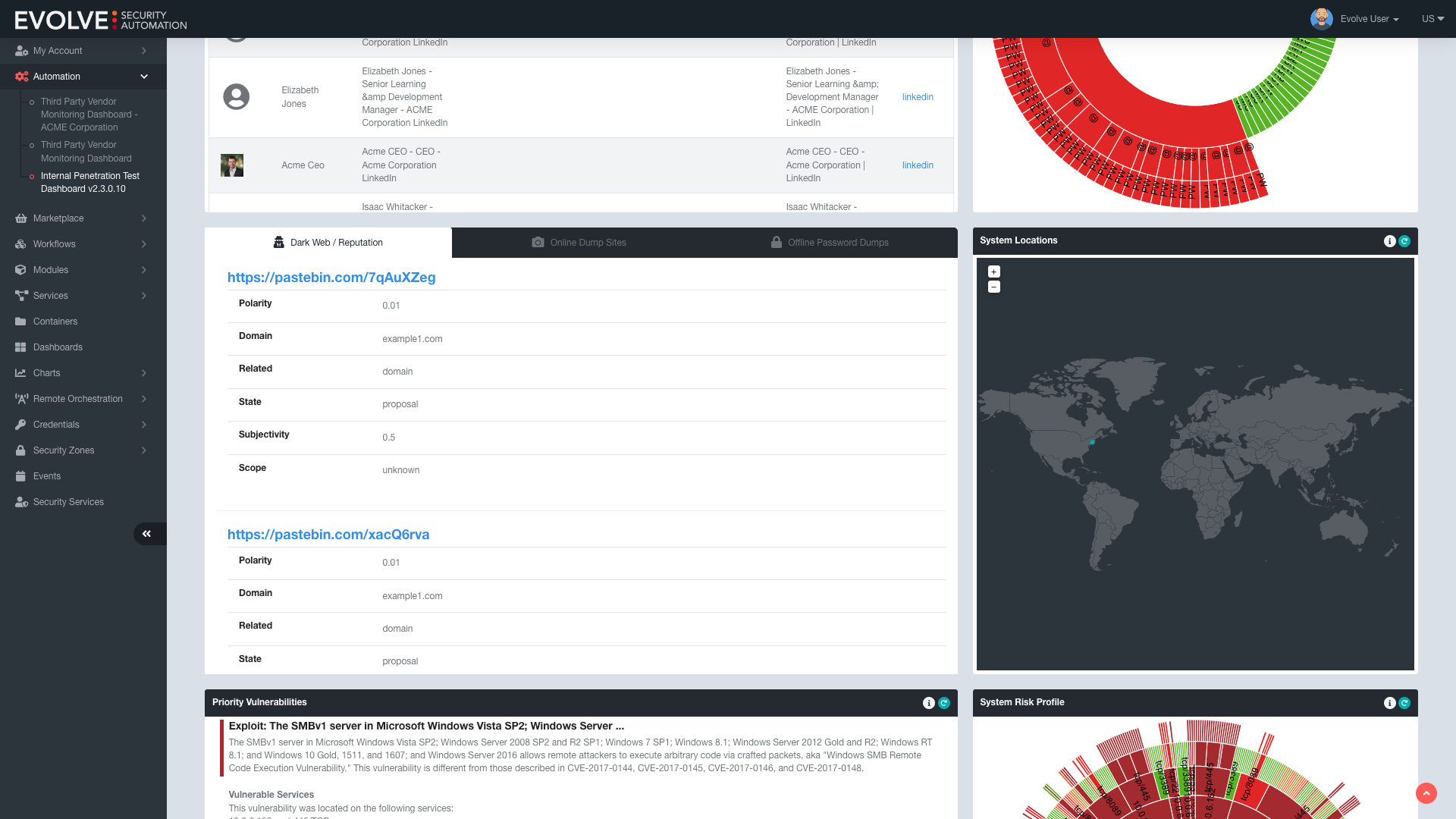
Conduct on-demand penetration testing that actively exploits vulnerabilities, providing you with in-depth visibility into your network.






Trusted by
With Evolve Automated Penetration
Testing you get a lot more coverage:
Vulnerability
Scan
Solution Capabilities
Phase 1: Internet Reconnaissance
Phase 2: Fingerprint and Scanning
Phase 3: Attack and Exploitation
Phase 4: Post-Exploitation & Lateral Movement
Phase 5: Reporting
Covarage Score
17%
0%
60%
8%
0%
59%
23%
100%
100%
100%
75%
87%
100%
92%
"This was the best penetration test that Threat Intelligence has ever delivered for our security team. It meets our objective and the outcome of the work is a high standard."
Jumar Pando
Information Security Lead
Mecca Brands





Stay Secure and Compliant with EvolvePT
With EvolvePT, you'll get on-demand testing, deep visibility into your network, and prioritised remediation of the biggest threats to your business. Plus, you'll have access to a team of Black Hat certified penetration testers ready to guide you through every step of the process. Stay secure, compliant, and on top of the ever-changing threat landscape with EvolvePT

Deep Coverage
Cover every possible attack scenario - from organization reconnaissance, man-in-the-middle attacks, automated exploitation, privilege escalation, and lateral movement, both in the cloud and across your organization’s security zones.

On-Demand
Schedule tests anytime, anywhere, at your convenience. 24/7 penetration testing services so that you can get the security assessment you need when you need it.

Prioritized Remediation
Focus on your biggest threats first. Get prioritized remediation recommendations from our expert security analysts.
Boost your vulnerability management with automation
Repetitive tasks lead to human errors, increasing the chances of your company being breached. Let us manage your most tedious and time-consuming tasks so your security team has the time to focus on their real job. EvolvePT automates just about everything, from reconnaissance, exploitation, lateral movement, post-exploitation activities, privilege escalation, password cracking and so much more. You don't have to hire more staff or pay large consulting fees because our team will already be on your side. Identifying vulnerabilities has never been easier.
Move forward with confidence
EvolvePT empowers you to make risk-adjusted decisions by testing your network against context-specific attacks. You'll have peace of mind knowing that your project is launched on a safe foundation and the latest threats (including the ones that just emerged) are covered. Instead of just providing a point-in-time snapshot of your environment, EvolvePT offers ongoing validation of your security posture and the data you need to create an effective long-term information security plan that supports the growth of your business.
Test your data no matter where it's stored
Your data is your most important asset, and we want to make sure it's secure - across all your environments. With EvolvePT's location-agnostic testing capabilities you know that your data is being tested from all angles, no matter where it's stored. Move your data around, change your infrastructure, we promise we won't get in your way.
- CMS and Web Attacks
- Contextual Attacks
- Real-time Exploit Locator
The team behind Evolve is certified to the highest standards with best-of-breed
certifications across the cybersecurity industry

The longest training at Black Hat,
over a decade

Our team is composed of highly experienced Principal Security Consultants,
all CREST Certified Penetration Testers

Consistently contributed to the
creation of the OWASP Standards
Key Features of EvolvePT
- Social Media Reconnaissance
- Email Verification
- Leaked Password
- System Fingerprinting
- Firewall Hole Identifier
- Admin Services Identifier
- Exposed Systems Identifier
- Vulnerability Scanning
- Cms And Web Attacks
- Contextual Attacks
- Password Cracking
- Credential Reuse
- Pass-The-Hash Attacks
- Automated Reporting
- And much more
FAQs
Got a question? We’re here to help.
-
What types of security tests does EvolvePT perform?
EvolvePT is mainly designed for performing external and internal infrastructure security testing.
-
How long does a typical EvolvePT scan take?
A typical EvolvePT scan takes anywhere from 2 days to a week, depending on the size of your network and the complexity of your infrastructure.
-
Is EvolvePT suitable for all types of businesses?
Yes, EvolvePT can be used by any type of business. Although designed mainly as an enterprise-grade solution, EvolvePT can be used in any business that wants to test its security posture. We have clients in a variety of industries including: financial services, education, healthcare, government, manufacturing, and more.
-
How frequently should I perform security testing with EvolvePT?
The answer to this is largely dependent on your organization and its security needs. For example, a retail merchant who handles millions of credit card transactions is most likely going to need more frequent pentesting than, say, a small, locally-owned dog groomer. However, most regulatory agencies require a pentest at least once a year. With EvolvePT, you can perform a pentest as often as you need to meet these requirements.
-
Can EvolvePT be customized to meet specific security needs?
Absolutely! Our clients have a wide range of customization options at their fingertips. You can customize the penetration testing method, scope, timing, and type of report to fit your needs.
-
Can EvolvePT scan web applications?
Yes, EvolvePT can scan web applications. To do this, simply incorporate the Application Security task into the application build steps. The test results will then be imported and displayed within the Pipeline.
-
Can EvolvePT perform both authenticated and unauthenticated scans?
Yes, EvolvePT can perform both authenticated and unauthenticated scans. However, EvolvePT cannot perform authenticated web application scans.
-
Does EvolvePT provide remediation guidance for detected vulnerabilities?
Yes, the EvolvePT report includes detailed remediation guidance for each vulnerability. The remediation guidance includes steps to remediate the vulnerability and references to the appropriate standards.
-
How does EvolvePT handle false positives?
EvolvePT uses a unique approach to eliminate false-positives during our automated pen testing process. After scannig for vulnerabilities, it uses all the detected exploits to attempt to break into our client's system, giving us a clear picture of which vulnerabilities pose a real risk to their infrastructure. This means that we only report on the actual threats that need to be addressed, rather than flooding our clients with false positives.
Furthermore, we take our reporting process one step further by including evidence of the breach in our reports. This includes a screenshot of the exploit that was used to gain unauthorized access to our client's system, providing a clear and tangible example of what needs to be addressed.
-
Is there a limit to the number of scans I can perform with EvolvePT?
There is no limit to the number of scans you can perform with EvolvePT. You can run as many scans as you need to meet your security requirements, and you can run them as frequently as you need to.
-
Can EvolvePT be used to test mobile applications?
No, Evolve cannot be used to test mobile applications. However, EvolveAST (our application security solution) can test mobile application APIs.
-
Can EvolvePT perform both authenticated and unauthenticated scans?
Yes, EvolvePT can perform both authenticated and unauthenticated scans. However, EvolvePT cannot perform authenticated web application scans.
-
What kind of licensing options are available for EvolvePT?
The license tiers are based on the number of live external and/or internal hosts to be tested each month. The target hosts can also be changed each month.
-
Does EvolvePT support compliance testing, such as PCI-DSS?
Yes, EvolvePT can be used to test compliance against PCI-DSS, HIPAA, NIST 800-53, ISO 27001, and GDPR.
-
What kind of reports does EvolvePT generate?
EvolvePT's reports are designed for clarity and ease of understanding by both executives and technical personnel. These reports include a summary of findings, a comprehensive technical report, an executive summary for board members, remediation recommendations with guidelines, real-time feedback, and a prioritized list of vulnerabilities based on exploitability. This structure allows for quick identification of critical vulnerabilities while minimizing false positives.
-
What kind of licensing options are available for EvolvePT?
The license tiers are based on the number of live external and/or internal hosts to be tested each month. The target hosts can also be changed each month.
-
Can EvolvePT scan APIs?
Our application security solution, EvolveAST scans APIs.
-
What kind of support and resources are available with EvolvePT?
Various support and resources are available with EvolvePT, including YouTube training videos that cover how to launch a penetration test, review reports, and analyze dashboards. Additionally, we offer managed services for clients who require extra assistance. By choosing EvolvePT as a managed service, you can contact our SOC team or email us for support. Our SOC team will ensure EvolvePT is properly set up and provide a report walkthrough, addressing any questions you may have. If you have a support agreement with us, we are more than happy to assist with troubleshooting and any other help you may need.
Strengthen Your Business with EvolvePT
With EvolvePT, you can prioritize and address the vulnerabilities that pose the most significant threats to your business. Schedule a demo tailored to your specific environment to see how EvolvePT can enhance your security strategy.