AWS penetration testing is the process of locating and exploiting security vulnerabilities in AWS cloud infrastructure and services. The goal of penetration testing is to identify and report on issues that could be exploited by an attacker to gain access to or disrupt an organization's AWS environment.
While the process may seem straightforward, it comes entwined with legal and technological constraints that can complicate its implementation.
There are a few things you should avoid when performing an AWS penetration test. In this article, we'll discuss four of the most common mistakes made during penetration testing, and how to avoid them.
What is AWS Penetration Testing?
Penetration testing is a highly effective security technique that can detect vulnerabilities in various environments, including web applications, networks, and cloud-based infrastructures. This kind of testing involves testing systems for potential security vulnerabilities, potential malicious activities, and misconfigurations.
Amazon Web Services is the most popular and widely used cloud platform by businesses to host their data and applications. As a result, the AWS cloud platform has become a target for malicious attacks. AWS lets its users test their AWS-based applications for security vulnerabilities using AWS penetration tests. These tests a comprehensive security assessment conducted by certified security professionals that evaluate the strength and robustness of an AWS-hosted environment. It also helps organizations to identify and correct any potential issues that could affect the security of their cloud-based infrastructure. Additionally, AWS penetration testing helps organizations to improve the overall security posture of their AWS environment and comply with relevant industry standards.
How is AWS Penetration Testing Different from Regular Penetration Testing?
Traditional pen testing techniques differ significantly from those used in AWS pen testing. The main difference lies in the system ownership. Since AWS is a subsidiary of Amazon, the cloud provider has certain policies and restrictions when it comes to pen testing on the AWS infrastructure. Traditional pen testing or ethical hacking methods would go against these policies. Moreover, pen testing on AWS infrastructure or hosted applications without authorization is a breach of the AWS acceptable usage policy.
Emerging Trends in AWS Security: 2023
At AWS re:Inforce 2023, Amazon made several key announcements:
- Amazon Verified Permissions: Amazon introduced "Verified Permissions," a service to manage permissions and authorization efficiently for secure application development.
- Amazon Inspector Code Scanning for Lambda Functions: Amazon Inspector expanded its capabilities to scan AWS Lambda functions for code vulnerabilities, providing actionable security findings.
- Amazon Inspector SBOM Export: Amazon Inspector now allows users to export Software Bill of Materials (SBOMs) for enhanced software supply chain visibility.
- Amazon CodeGuru Security: "CodeGuru Security" offers a set of APIs for seamless code vulnerability identification and in-context patching.
- Amazon EC2 Instance Connect Endpoint: Amazon EC2 now supports SSH or RDP connectivity to instances in private subnets through the EIC Endpoint.
- AWS Built-in Partner Solutions: AWS introduced co-developed "built-in partner solutions" to streamline cloud development and deployment.
- AWS Cyber Insurance Partners: AWS collaborated with cyber insurance partners to simplify obtaining cyber insurance by sharing security reports from AWS Security Hub.
- AWS Global Partner Security Initiative: AWS announced the Global Partner Security Initiative to jointly develop end-to-end security solutions with Global System Integrators (GSI) partners.
- Amazon Detective Finding Groups: Amazon Detective now includes Amazon Inspector findings in its finding groups feature for improved security incident investigation.
- AWS Private Certificate Authority Connector for Active Directory (Pre-announce): AWS Private CA will soon launch a Connector for Active Directory to simplify PKI management.
- AWS Payment Cryptography: AWS Payment Cryptography simplifies cryptographic operations in cloud-hosted payment applications, aligning with PCI standards.
- AWS WAF Fraud Control: AWS WAF Fraud Control introduces Account Creation Fraud Prevention for securing account sign-up pages.
- AWS Security Hub Automation Rules: AWS Security Hub now supports automation rules for updating and managing findings in real-time.
- Amazon S3 Dual-Layer Server-Side Encryption: Amazon S3 introduced dual-layer server-side encryption for enhanced security compliance.
- AWS CloudTrail Lake Dashboards: AWS CloudTrail Lake now offers dashboards for visualizing and analyzing audit and security logs.
- AWS Well-Architected Profiles: AWS Well-Architected introduced "Profiles" for tailored workload reviews based on specific business goals.
Source: AWS
What Can and Cannot Be Tested Using AWS Pen Testing?
AWS allows users to completely test user-operated services, which include cloud solutions that users can deploy and configure themselves, such as EC2 instances. Users can test these instances except for tests such as Denial of Service (DoS) or any other form of attack that disrupts continuity and availability.
Whereas, vendor-operated services are cloud offerings that are managed or configured by third-parties. In such cases, AWS only allows pen testing of the configuration and implementation of the cloud environment. The underlying infrastructure and all other areas are not allowed to be tested.
Amazon Web Services (AWS) customers don’t need prior permission to perform a security assessment for the following services:
- Amazon Aurora
- Amazon RDS
- Amazon CloudFront
- AWS Fargate
- Amazon EC2 instances, Elastic Load Balancers, and NAT Gateways
- Amazon API Gateways
- Amazon Elastic Beanstalk environments
- Amazon Lightsail resources
- AWS Lambda and Lambda Edge functions
Pen testers can do security checks on certain parts of AWS EC2 instances, such as:
- Vulnerabilities and misconfigurations in the API
- The company’s web applications that are hosted on EC2 instances
- Programming logic and business flows
- Virtual machines and operating systems that have been deployed on EC2 instances
The following AWS components should not be tested by any user:
- AWS-provided services, systems, servers, or applications
- Physical hardware devices, facilities, infrastructure, and tech that AWS owns
- All EC2 instances that are owned by a vendor or another organization
- Security appliances that are managed by third-parties or other organizations
Common Mistakes to Avoid When Performing AWS Penetration Testing
When it comes to AWS penetration testing, there are a few things you want to avoid. These mistakes can cost you time and money, and can even jeopardize the security of your systems. Avoid these oversights for a successful AWS pen test:
1. Overlooking the Basics
Make sure you have a good understanding of the AWS platform before you start testing. The Amazon cloud works on the shared responsibility model. This means that AWS is responsible for the security of your cloud environment and you are responsible for the security in your own environment. Therefore, before starting the AWS pen test, it is crucial to have a good understanding of exactly how much security you're responsible for and what you can expect from the provider.
Take a look at this diagram that shows the shared responsibility model:
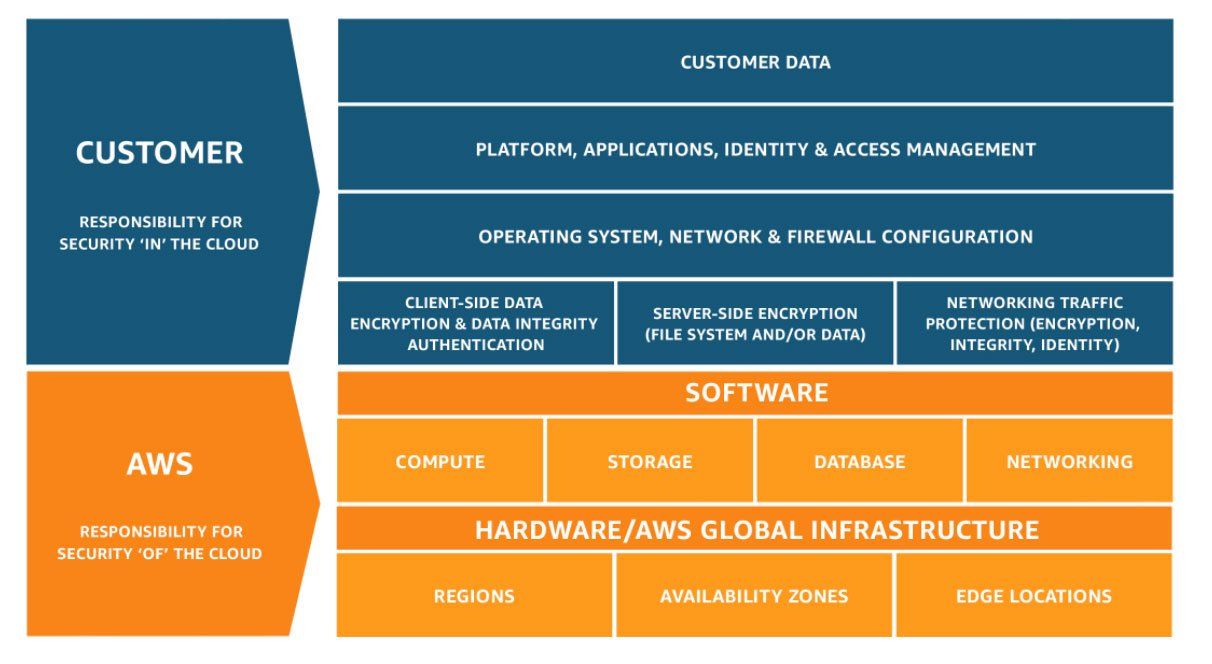
Source: Amazon
2. Not Knowing Your AWS Limits
As mentioned in the previous section, AWS penetration testing is different from traditional pen tests. Violating AWS policies can lead to a direct intervention from the provider. Therefore, know exactly what you're allowed to test in the cloud environment and how to do it.
3. Making S3 Buckets Public
On AWS, you can keep your S3 buckets public. This means that anyone can access your bucket and any information within it. While this feature makes your data more accessible, it also makes your data more vulnerable to data breaches. To limit unintentional public exposure of your data, use Amazon S3's 'block public access function.'
4. Granting Too Many Permissions
This is an idea that's often disregarded by many organizations while testing. They give user entities more permissions than they need. Another common mistake is not defining user groups in terms of the level of access needed. Permission management is critical for the success of any pen test you want to carry out in the AWS environment.
Conclusion
AWS penetration testing is an essential tool for any organization that relies on the use of cloud computing services. With the ability to conduct tests within virtual environments, you can identify and address any potential security vulnerabilities before they become a problem. Leveraging AWS penetration testing lets you quickly assess your system configurations, detect any malicious activity, and take action to mitigate any risks.
Threat Intelligence’s unique approach to automated penetration testing helps enterprises identify and mitigate risks quicker and more efficiently. Moreover, our suite of automated testing tools integrate with your existing AWS security infrastructure to provide a comprehensive solution for enterprise cloud security. Our world-class security analysts, and consultants, provide actionable, accurate and reliable results that'll help you better manage your cloud infrastructure. To learn more,
contact us for a free demo today.






