David Glimore
Cyber Security Analyst at Threat Intelligence and artificial intelligence researcher.
David Gilmore • July 12, 2024


David Glimore
Cyber Security Analyst at Threat Intelligence and artificial intelligence researcher.
The Conti ransomware gang, a formidable force in the world of cybercrime, has left an indelible mark on the cybersecurity landscape. Emerging around December 2019, Conti quickly became notorious for its sophisticated attacks, large ransom demands, and ruthless tactics. Despite reports of the group disbanding, the threat posed by Conti's ransomware-as-a-service (RaaS) model persists, with various cybercriminals continuing to deploy its malicious software. This analysis provides a comprehensive overview of the Conti ransomware gang, including its history, attack methodologies, and indicators of compromise (IOCs).
The Conti ransomware gang is believed to have ties to the infamous Ryuk ransomware, sharing several code similarities. Initially, Conti operated in a manner similar to other ransomware groups, encrypting victims' data and demanding a ransom for decryption. However, Conti distinguished itself with its highly efficient and organised operations.
Conti's operations were characterised by their "big game hunting" approach, only targeting large organisations across various sectors, including healthcare, education, and critical infrastructure. The gang's aggressive tactics included exfiltrating data before encryption, a method known as double extortion. This tactic ensured that even if victims had backups to restore their systems, they would still face the threat of their sensitive data being leaked publicly if they did not pay the ransom. A tactic used by many ransomware groups now.
In early 2022, leaks from within the Conti organisation provided insight into the group's operations. These leaks revealed the gang's internal communications, strategies, and even the identities of some members. Despite the subsequent reports of the group disbanding, the RaaS model employed by Conti ensures that its ransomware continues to be a significant threat, as various affiliates can still use and distribute the ransomware and profit from its execution.
Conti ransomware is known for its speed and efficiency in encrypting data. It leverages a combination of AES-256 and RSA-4096 encryption algorithms to encrypt victims' files, making decryption without the correct key virtually impossible. Conti typically gains initial access to victims' networks through various means, including phishing emails, malicious attachments, and exploiting vulnerabilities in remote desktop protocol (RDP) services.
Once inside a network, Conti exhibits the following behaviours:
Conti's operational success can be attributed to its sophisticated tactics and techniques, which include:
Conti often gains access to networks through malicious Word/Excel documents with embedded scripts that use the TrickBot malware.. Conti also uses spear phishing campaigns, phone calls, fake software products promoted via sponsored ads, Zloader, and stolen or weak credentials for RDP protocol.
Conti typically runs a ‘getuid’ payload before using a more aggressive payload to reduce the possibility of triggering any endpoint protection. Conti actors have used Kerboros attacks in attempts to obtain Administrator file hashes, using Router Scan, a penetration testing tool and other hacking tools. Legitimate Windows tools such as PowerShell and Command Prompt are also used to execute command line commands and scripts and use API calls during execution.
Conti actors are known to use a wide range of techniques to maintain persistence on victims' systems. Those techniques include modifying registry keys, adding entries to the Run or RunOnce keys, which automatically execute specified programs during system startup.
Conti threat actors also utilise scheduled tasks to maintain persistence, for example executing malware on boot or during system events. An example of such a technique would be:
The ransomware group is known to install their malware as Windows services, inject dll files and use various commands to maintain persistence, Conti have been seen to regularly use the following commands:
reg add HKCU\Software\Microsoft\Windows\CurrentVersion\Run /v <name> /t REG_SZ /d <path to malware>
schtasks /create /tn <task name> /tr <path to malware> /sc onstart /ru system
sc create <service name> binPath= "<path to malware>"
sc start <service name>
net user <username> <password> /add
net localgroup administrators <username> /add
rundll32.exe <path to malware>,<exported function>
psexec \\<target IP> -u <username> -p <password> -s -d <path to malware>
certutil -encode <input file> <output file>
certutil -decode <encoded file> <decoded file>
wevtutil cl Application
wevtutil cl Security
wevtutil cl System
wmic process call create "<path to malware>"
wmic useraccount where name='<username>' set PasswordExpires=false
These commands and techniques demonstrate the sophistication and variety of methods Conti employs to ensure persistence on compromised systems (CISA) (Unit 42) (The Security Validation Platform).
In addition Conti are known to hijack dll files in locations where legitimate applications might load during startup. This effectively hijacks the legitimate loading process to execute their malicious code. Placing files in the startup folder and using Bootkits or Rootkits.
Conti Adversaries often leverage external-facing remote services to initially access and persist within a network. Remote services such as virtual private networks (VPNs), Citrix, and other access mechanisms allow users to connect to internal enterprise network resources from external locations. There are often remote service gateways that manage connections and credential authentication for these services.
The COnti threat actors have been known to use many different lateral movement techniques once inside a corporate network. Those techniques include:
Despite reports of the Conti gang's disbandment, the ransomware itself continues to be a significant threat. The RaaS model ensures that the ransomware can be deployed by various cybercriminals, perpetuating its use and impact.
In
Recorded Futures Ransomware Tracker, published on 10th June 2024, Conti was rated the second most prolific ransomware:
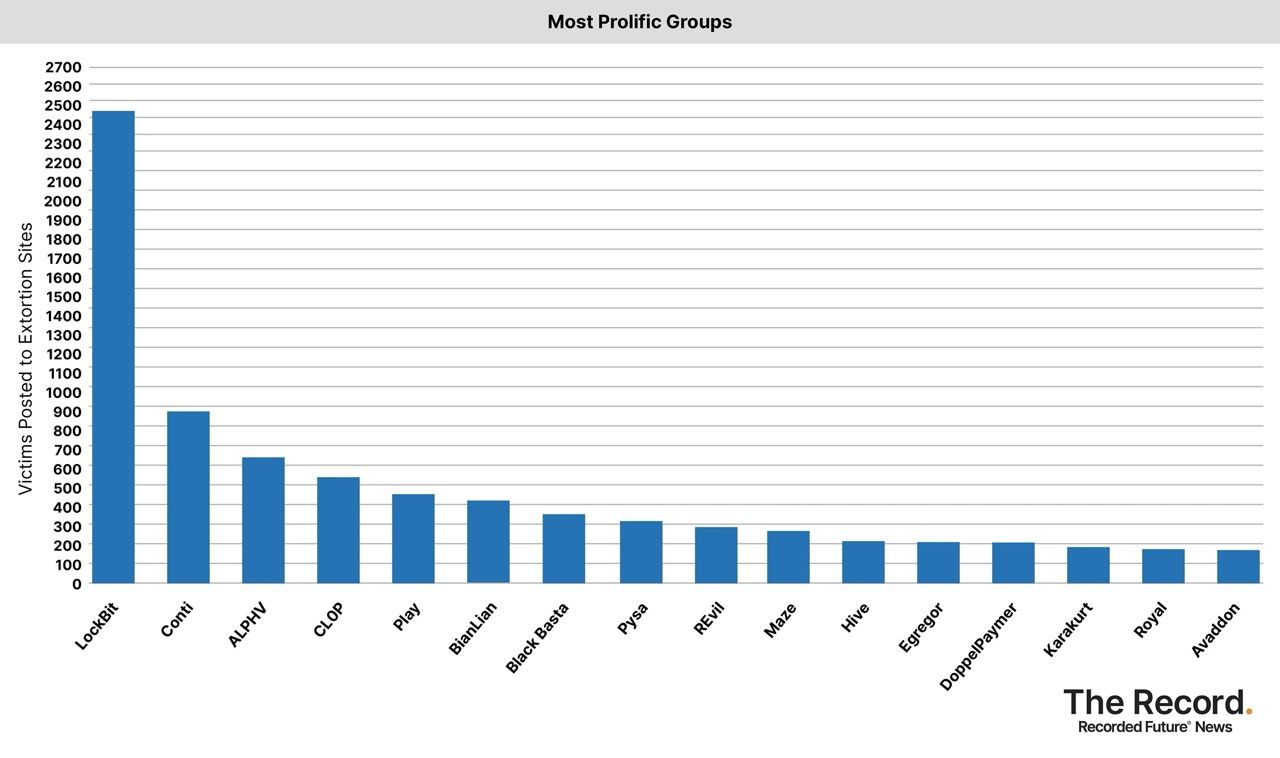
Recent attacks have demonstrated that Conti ransomware remains a favoured tool among cybercriminals, with its efficient encryption and double extortion tactics proving highly effective.
The following table summarises key IOCs associated with Conti ransomware attacks:
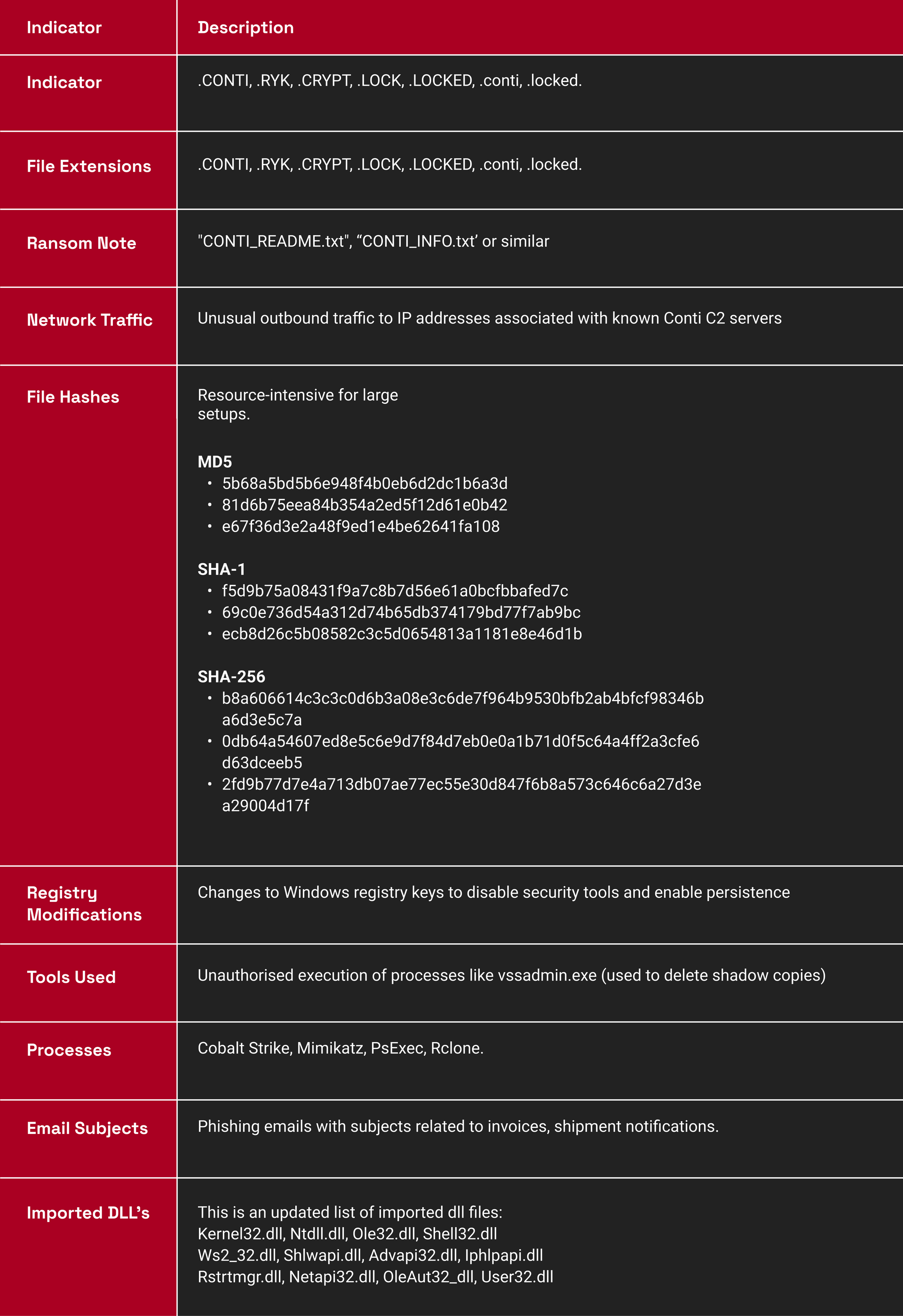
The Conti ransomware gang has left a lasting legacy. While the group's core members may have dispersed, the ransomware they developed continues to pose a substantial threat. Cybersecurity professionals must remain vigilant, employing robust security measures and staying informed about the latest IOCs associated with Conti ransomware. By understanding the history, tactics, and ongoing risks related to Conti, organisations can better protect themselves against this persistent and evolving threat.
Contact us today for a personalised consultation to discover how the Evolve suite of products can meet your specific security needs. Our team will work with you to assess your current security posture, identify potential vulnerabilities, and tailor a solution that maximises protection and efficiency.
Schedule a consultation with one of our experts today!
Related Content