Recently, a significant vulnerability has been identified in Fortinet's FortiOS and FortiProxy. This vulnerability, tracked as CVE-2024-21762, poses a severe risk of unauthenticated remote code execution (RCE) and is currently being targeted in the wild.
Our team performed an investigation and developed custom IOCs to detect the exploitation of this vulnerability. Read on to understand the details of this critical security concern and the necessary steps to protect your systems.
Overview
The vulnerability, assigned a CVSS score of 9.6, stems from an out-of-bounds write flaw in sslvpnd, the component responsible for handling SSL VPN functions, which means that a LOT of companies are exposed. An attacker can exploit this weakness through specially crafted HTTP requests, potentially executing arbitrary code or commands.
Immediate Action Required
Given the critical nature of this vulnerability and its potential exploitation in the wild, we strongly urge all users to apply the recommended upgrades or migrations as outlined below.
Affected Versions and Solutions
FortiOS:
- Not affected: 7.6
- Upgrade to 7.4.3 or above: 7.4.0 through 7.4.2
- Upgrade to 7.2.7 or above: 7.2.0 through 7.2.6
- Upgrade to 7.0.14 or above: 7.0.0 through 7.0.13
- Upgrade to 6.4.15 or above: 6.4.0 through 6.4.14
- Upgrade to 6.2.16 or above: 6.2.0 through 6.2.15
- Migrate to a fixed release: 6.0 all versions
FortiProxy:
- Upgrade to 7.4.3 or above: 7.4.0 through 7.4.2
- Upgrade to 7.2.9 or above: 7.2.0 through 7.2.8
- Upgrade to 7.0.15 or above: 7.0.0 through 7.0.14
- Upgrade to 2.0.14 or above: 2.0.0 through 2.0.13
- Migrate to a fixed release: 1.2 all versions, 1.1 all versions, 1.0 all versions
For detailed information and upgrade instructions, please refer to Fortinet's official advisory https://www.fortiguard.com/psirt/FG-IR-24-015.
Custom Post-Breach IOCs by Threat Intelligence
Despite exploits not being publicly available at the time of writing, our SOC performed an in-depth analysis and proactively created custom IOCs that could be used to identify post-breach activities from threat actors.
These IOCs are based on a previous Digital Forensics and Incident Response (DFIR) investigation performed by Threat Intelligence that involved a series of Fortinet firewalls being compromised via another critical vulnerability.
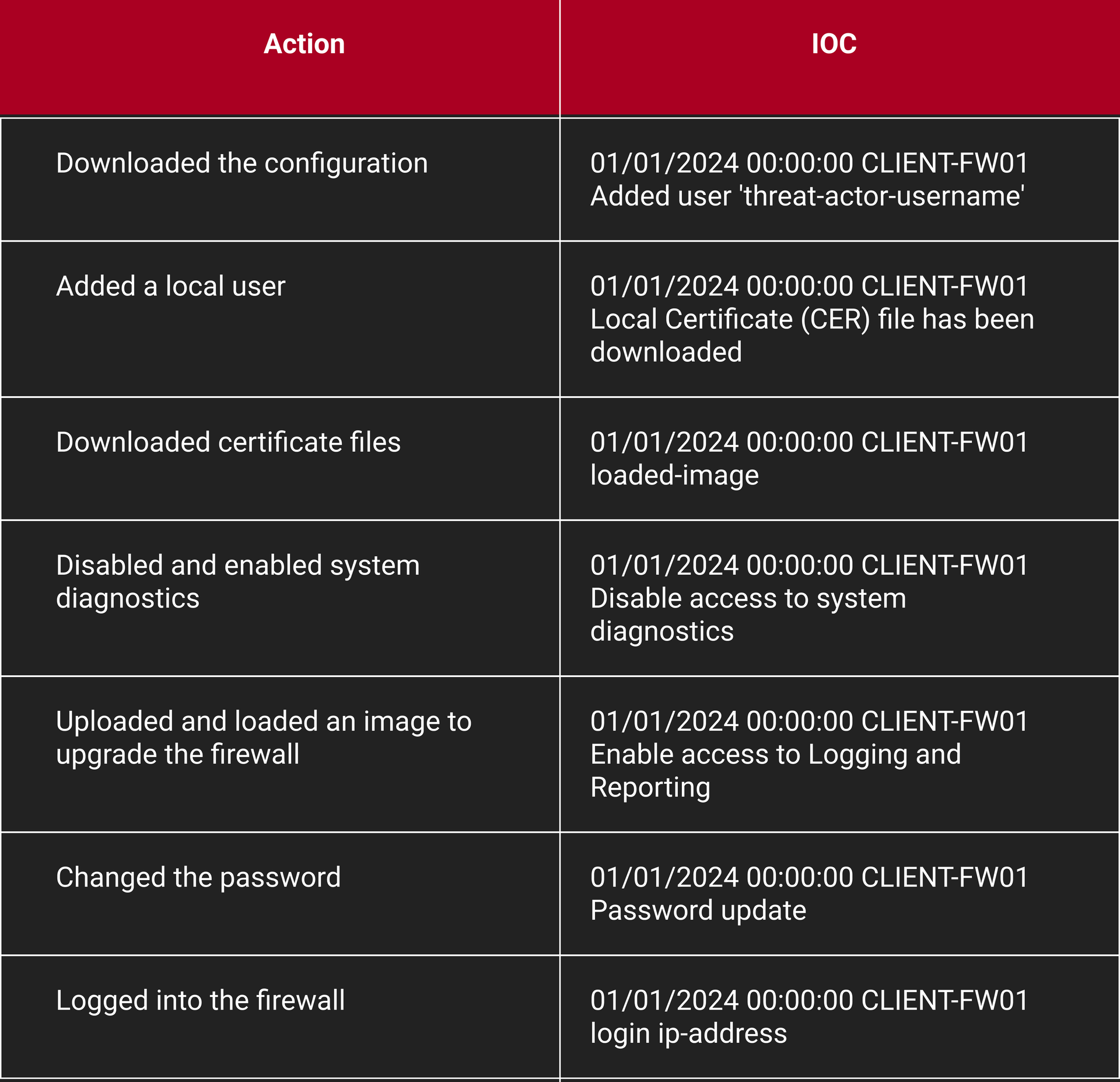
During this breach, the threat actors performed the following actions to gain access and maintain persistence to the Fortinet devices:
- Downloaded the configuration
- Added a local user
- Downloaded certificate files
- Disabled and enabled system diagnostics
- Disabled and enabled logging and reporting
- Uploaded and loaded an image to upgrade the firewall
- Changed the password
- Logged into the firewall
The IOCs generated by the Fortinet firewalls for these activities are shown below:
- 01/01/2024 00:00:00 CLIENT-FW01 Added user 'threat-actor-username'
- 01/01/2024 00:00:00 CLIENT-FW01 Local Certificate (CER) file has been downloaded
- 01/01/2024 00:00:00 CLIENT-FW01 loaded-image
- 01/01/2024 00:00:00 CLIENT-FW01 Disable access to system diagnostics
- 01/01/2024 00:00:00 CLIENT-FW01 Enable access to Logging and Reporting
- 01/01/2024 00:00:00 CLIENT-FW01 Password update
- 01/01/2024 00:00:00 CLIENT-FW01 login ip-address
Our team recommends monitoring for the above IOCs to identify any post-exploitation activity in your environment. In addition to the above IOCs, it is also recommended that you monitor for IOCs related to other unusual configuration changes.
Additional Intelligence
Coincidentally, Fortinet recently announced the activities of Chinese state-sponsored threat actors called Volt Typhoon. These actors have been targeting vulnerabilities in FortiOS to deploy custom malware named COATHANGER. Interestingly, just a day before Fortinet's disclosure, the US government released a new set of Indicators of Compromise (IOCs) related to this threat actor group. This correlation suggests a potential connection between the two announcements and the critical vulnerability in Fortinet's system, which directly aligns with the modus operandi of the Volt Typhoon threat actor group.
This highlights the importance of prompt action to secure your systems against these emerging threats.
Volt Typhoon IOCs from the US Government
The following is the latest threat intelligence from the US Government regarding Volt Typhoon. Threat Intelligence recommends that your SOC team monitor for the following IOCs relating to identify post-breach activities.
Summary of Volt Typhoon IOCs:
Files:
SMSvcService.exe
- MD5: b1de37bf229890ac181bdef1ad8ee0c2
- SHA-1: ffdb3cc7ab5b01d276d23ac930eb21ffe3202d11
- SHA-256: 99b80c5ac352081a64129772ed5e1543d94cad708ba2adc46dc4ab7a0bd563f1
- SHA-512: e41df636a36ac0cce38e7db5c2ce4d04a1a7f9bc274bdf808912d14067dc1ef478268035521d0d4b7bcf96facce7f515560b38a7ebe47995d861b9c482e07e25
BrightmetricAgent.exe
- MD5: fd41134e8ead1c18ccad27c62a260aa6
- SHA-1: 04423659f175a6878b26ac7d6b6e47c6fd9194d1
- SHA-256: edc0c63065e88ec96197c8d7a40662a15a812a9583dc6c82b18ecd7e43b13b70
- SHA-512: df55591e730884470afba688e17c83fafb157ecf94c9f10a20e21f229434ea58b59f8eb771f8f9e29993f43f4969fe66dd913128822b534c9b1a677453dbb93c
Hashes:
- MD5: 3a97d9b6f17754dcd38ca7fc89caab04
- SHA-1: ffb1d8ea3039d3d5eb7196d27f5450cac0ea4f34
- SHA-256: eaef901b31b5835035b75302f94fee27288ce46971c6db6221ecbea9ba7ff9d0
- SHA-512: d99941e4445efed5d4e407f91a9e5bba08d1be3f0dab065d1bfb4e70ab48d6526a730233d6889ba58de449f622e6a14e99dab853d40fc30a508627fd2735c973
IP Addresses:
- 203.95.8.98
- 203.95.9.54
Domains:
- pdsguam[.]biz
We recommend continuous monitoring for any signs of these indicators in your systems and network traffic moving forward.
For the full CISA report, visit:
https://www.cisa.gov/news-events/analysis-reports/ar24-038a
What is an out-of-bounds-write vulnerability?
An out-of-bounds write vulnerability occurs when a software product writes data beyond the intended boundaries of a designated storage area, either at the beginning or the end. Picture it like writing beyond the margins of a page – it's not supposed to happen, and when it does, problems arise.
What Happens:
This misstep in coding can lead to various issues, such as data corruption, system crashes, or even unauthorized code execution.
How It Occurs:
The software may inadvertently manipulate an index or perform pointer arithmetic that points to a memory location beyond the boundaries of the allocated space. When the product tries to write information there, it creates undefined or unexpected outcomes.
Alternate Term: Memory Corruption
Sometimes, you might hear it referred to as "memory corruption". This term is often used when data is written outside the expected buffer limits, resulting in unintended consequences. It could stem from issues like incorrect pointer arithmetic or accessing invalid pointers due to incomplete initialization or memory release.
Source:
MITRE, Common Weakness Enumeration (CWE)
Who is the threat actor group Volt Typhoon?
Volt Typhoon is a Chinese cyber espionage group, targeting critical American infrastructure.
- Objective: Volt Typhoon's focus shifted from intelligence gathering to potential digital sabotage, raising concerns about disruptions in critical communications infrastructure during future crises.
- Geopolitical Implications: The group's activities align with heightened tensions between China and the United States, especially over the Taiwan issue. The possibility of cyberattacks across the Pacific in the event of conflict is a significant concern.
- Botnet Tactics: Volt Typhoon employed a botnet composed of vulnerable digital devices worldwide, concealing downstream attacks on sensitive targets. This strategy limited the visibility of cyber defenders monitoring foreign footprints.
- Operational Security: The group, linked to China, has a history of denying hacking allegations. Operational security measures, such as using botnets, indicate an effort to cover tracks and avoid public scrutiny.
Source: Reuters
Need help with your security monitoring?
Elevate your defense strategy with EvolveXDR. Get unlimited EDR agents, ensuring comprehensive endpoint coverage without added costs. Our solution delivers immediate security monitoring, empowering you to swiftly detect and respond to threats. Plus, with automated detection and response capabilities, you can streamline your security operations for enhanced efficiency. Partner with our 24/7 Evolve SOC, staffed by seasoned cybersecurity specialists, to bolster your defenses and safeguard your organization against evolving threats.
Try a free demo of EvolveXDR today.
Explore the entire Evolve suite of products
here, designed to give your enterprise complete protection from evolving threats.






