Sam Panicker
Technical GRC Specialist at Threat Intelligence, IRAP Assessor, ISO 27001 Lead Implementer, Certified Information Systems Security Professional (CISP), ISACA Certified in Risk and Information Systems Control (CRISC).
Anupama Mukherjee • May 8, 2024


Sam Panicker
Technical GRC Specialist at Threat Intelligence, IRAP Assessor, ISO 27001 Lead Implementer, Certified Information Systems Security Professional (CISP), ISACA Certified in Risk and Information Systems Control (CRISC).
Since the National Institute of Standards and Technology (NIST) released its Cybersecurity Framework in 2014, it has become one of the most widely used tools for managing cybersecurity risk. The framework provides a flexible and adaptable approach to cybersecurity that can be tailored to the specific needs of any organization. In this blog post, we'll provide an overview of the NIST Cybersecurity Framework and explain how you can use it to improve your organization's cybersecurity posture.
This post has been written with the help of our GRC team.
There are several different types of cybersecurity frameworks, NIST being one of the most widely used. But what is a cybersecurity framework and why is it used?
A cybersecurity framework is a set of guidelines that can be used to guide the protection strategies that are put into place for a company or organization. A set of documented processes and best practices, they're used to design the IT security policy of an organization and to create a system that is able to detect and respond to potential security threats. Basically, they help organizations address cybersecurity risks and vulnerabilities in an organized and efficient manner.
Cybersecurity frameworks are usually developed through a process of collaboration involving multiple stakeholders such as government bodies, businesses, and third-party experts. In order to be effective, these frameworks must be tailored specifically to the needs of the organization in question. Some examples of cybersecurity frameworks that are currently in use include NIST,
HIPAA, ISO 27001, GDPR,
PCI DSS, NERC-CIP, FISMA, and more.
Now let's get into the details of the NIST cybersecurity framework. NIST stands for the National Institute of Standards and Technology. It is an organization that eases the way for the government to improve its ability to develop, manage, and use information technology and its related systems. The NIST Cybersecurity Framework provides a flexible and adaptable approach to help organizations manage cybersecurity risk. The framework helps organizations identify, assess, and respond to risks in a way that aligns with their business goals and objectives. By using the framework, organizations can improve their cybersecurity posture and better defend against cyber attacks.
The NIST Cybersecurity Framework was initially put in place after US President Barack Obama signed Executive Order 13636 to better manage the security of its critical infrastructure. Under this Executive Order, NIST was required to develop a framework using existing standards, guidelines, and practices to minimize the risk to the critical infrastructure. Originally created for private-sector owners and operators of critical infrastructure, NIST is now adopted by federal agencies, businesses, and educational institutions alike and from all over the world.
The journey to Version 2.0 of the NIST Cybersecurity Framework commenced in 2022, propelled by a renewed focus on addressing the dynamic landscape of cyber threats, technological advancements, and evolving industry practices. Recognizing the need to stay ahead of emerging challenges, NIST embarked on an iterative and collaborative process to develop and refine the framework.
Drawing upon lessons learned from Version 1.1 and insights gleaned from ongoing cybersecurity initiatives, NIST initiated a series of drafts, discussions, and feedback mechanisms to inform the development of Version 2.0. This iterative approach allowed NIST to incorporate the latest advancements in cybersecurity technologies and methodologies, ensuring that the framework remained relevant and adaptable to the evolving needs of cybersecurity stakeholders.
Throughout the journey to Version 2.0, NIST actively solicited feedback from a diverse range of stakeholders, including government agencies, industry partners, academia, and cybersecurity professionals. This inclusive approach fostered a robust exchange of ideas and perspectives, enabling NIST to address emerging challenges and anticipate future trends in cybersecurity risk management.
Using the collective expertise and insights of the cybersecurity community, NIST iteratively developed and refined Version 2.0 of the Cybersecurity Framework, ensuring that it remained a valuable resource for organizations seeking to enhance their cybersecurity resilience in an increasingly complex threat landscape.
Here’s a quick NIST Cybersecurity Framework Summary and detailed breakdown:
The NIST Cybersecurity Framework is made up of the following core elements - Functions, Categories, Subcategories, and References.
Functions are used to organize basic cybersecurity concepts and activities. They help an organization demonstrate its cybersecurity risk management capabilities. Categories divide a Function into groups of cybersecurity outcomes that are closely related to programmatic needs and specific activities. Subcategories are used to further divide categories into more specific outcomes of technical and/or management activities. Lastly, informative resources are a set of guidelines, standards, and best practices that are common across critical infrastructure sectors and show how to achieve the outcomes associated with each Subcategory.
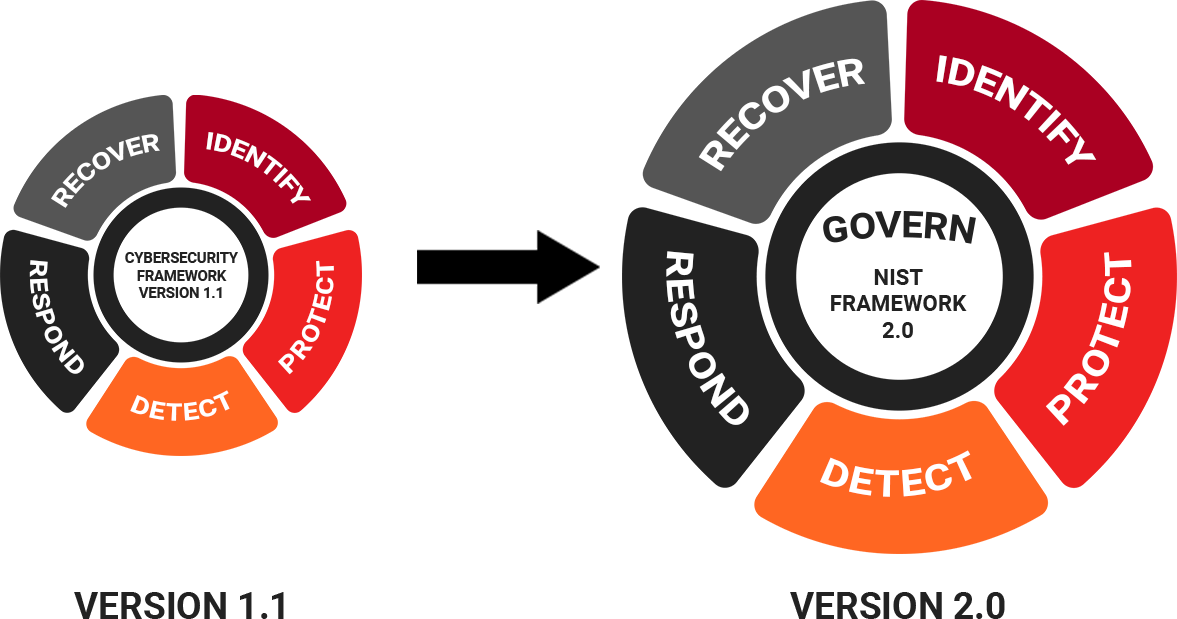
NIST Cybersecurity Framework (CSF) 2.0 offers a structured approach to managing cybersecurity risks, emphasizing proactive measures to enhance organizational resilience against evolving threats. At its core are six key Functions: GOVERN, IDENTIFY, PROTECT, DETECT, RESPOND, and RECOVER.
This Function establishes the organization's cybersecurity risk management strategy, policies, and expectations. It ensures alignment with broader enterprise risk management strategies and fosters a comprehensive understanding of organizational context, roles, responsibilities, and authorities.
By understanding current cybersecurity risks and organizational assets, this Function enables prioritization of efforts consistent with the risk management strategy. It encompasses the identification of improvement opportunities for policies, plans, and procedures supporting cybersecurity risk management.
This Function focuses on implementing safeguards to manage cybersecurity risks effectively. It secures assets to prevent or mitigate adverse events, covering aspects such as identity management, access control, awareness training, data security, and technology infrastructure resilience.
Detecting cybersecurity attacks and compromises in a timely manner is the focus of this Function. It facilitates the discovery and analysis of anomalies, indicators of compromise, and other adverse events, supporting incident response and recovery activities.
Actions taken in response to detected cybersecurity incidents fall under this Function. It includes incident management, analysis, mitigation, reporting, and communication, aimed at containing the effects of incidents and minimizing disruption.
This Function focuses on restoring assets and operations affected by cybersecurity incidents. It supports the timely restoration of normal operations, reducing the impact of incidents, and facilitating effective communication during recovery efforts.
A Profile in the NIST Cybersecurity Framework is a detailed description of the current state or the desired target state of a cybersecurity activity. The Current Profile describes the cybersecurity outcomes that are being achieved right now, whereas the Target Profile indicates the outcomes that need to be achieved in order to meet the organizational risk management goals.
In other words, the Framework Profile is used to integrate the Functions, Categories, and Subcategories into the organization's business requirements, resources, and risk tolerance. Organizations can use it to develop a blueprint for risk reduction that takes into consideration the organizational goals, legal and regulatory requirements, industry best practices, and risk management priorities.
Profiles also help to assess the resources required to achieve cybersecurity objectives in a cost-effective and prioritized manner. For instance, a comparative study of the Current and Target Profiles mentioned above can highlight the gaps that must be filled in order to achieve the desired outcomes.
The Framework Implementation Tiers describe how an organization views cybersecurity risk and how it is addressed. They describe the organization's current risk management strategy in relation to the framework's characteristics, such as how repeatable, threat aware, and adaptive the strategy is. They range from Partial (Tier 1) to Adaptive (Tier 4).
Tier 1 - Partial: The organization's risk management strategy is not formalized and is managed haphazardly and occasionally reactively. In addition, the organization is not aware of the risks it faces.
Tier 2 - Risk-Informed: The organization may not have a formalized risk management strategy for managing security risks. The management is in charge of managing cybersecurity risks as they arise.
Tier 3
- Repeatable: The organization has a repeatable and formalized process for managing cybersecurity risks and a clearly defined security policy.
Tier 4 - Adaptable: At this stage, an organization's cybersecurity policies will be adapted based on lessons learned and driven by analytics to provide insights and best practices. The organization continuously improves its security strategy based on the security incidents it experiences and also shares this knowledge with the wider network.
Staying ahead of threats requires more than just reactive measures—it demands proactive, strategic planning. The Govern function of the updated NIST framework emphasizes the cultivation of a risk-aware culture within organizations. At its core, this function empowers leaders to leverage risk management as a strategic asset, aligning security objectives with overarching business goals.
We sat down with our technical GRC team to uncover the nuances of this pivotal addition and its implications for organizational resilience.
Let's look at the key elements of the Govern function:
Understanding the intricacies of your organization's ecosystem is paramount in order to secure it. This entails identifying valuable assets, comprehending potential threats and attack vectors, defining desired outcomes, and navigating the maze of legal, regulatory, and contractual obligations. It's about gaining a holistic view of your organization's risk landscape.
"You need to understand what you're trying to protect, and why you should protect it before you start implementing secutity controls and policies." , said Sam Panicker, technical GRC specialist at Threat Intelligence.
NIST 2.0 prompts organizations to define their risk appetite and tolerance levels, establish protocols for breach response, and implement standardized methods for risk assessment and prioritization. It's about being proactive rather than reactive in the face of threats.
Clarity in roles and responsibilities is essential for a well-oiled risk management machinery. This involves delegating who is accountable for each aspect of the risk management process, fostering a security-centric culture, and ensuring adequate resource allocation. It's about empowering individuals to take ownership of cybersecurity within their spheres of influence.
This category is about laying down the ground rules for effective risk governance. Policies serve as the guiding beacon in navigating the complex cybersecurity landscape. NIST 2.0 emphasizes the establishment, review, and adaptation of risk management policies to reflect evolving threats and organizational dynamics.
Vigilance is key to staying ahead of emerging threats. Regular review and adjustment of risk management strategies enable organizations to course-correct and optimize their security posture. Examining what is and is not working for your company can help you stay flexible and agile when faced with evolving challenges.
In an interconnected world, the security of your supply chain is as critical as your internal defenses. NIST 2.0 underscores the importance of robust supply chain risk management practices, including supplier vetting, policy formulation, and integration into incident response planning. It's about extending your security perimeter to encompass external partnerships and collaborations.
"Sometimes, the weakest link in the chain is a supplier and not an internal system.", Sam noted.
In essence, the Govern function of NIST 2.0 equips organizations with the tools and frameworks to navigate the complex cybersecurity landscape with confidence and foresight.
The benefits of the NIST Cybersecurity Framework can be summarized in the following points:
First, the Framework helps organizations to better understand and manage their cybersecurity risks. It helps to strengthen your organization's approach to secure assets and data. And since the NIST Framework is built on the experience of security experts from across the world, following the Framework will help organizations to achieve a global standard of cybersecurity.
Second, it provides a common language for communication between different stakeholders about cybersecurity risks and how to mitigate them. This improves communication between different stakeholders and leads to better collaboration and ultimately a safer organization.
Third, the Framework can be used to assess the effectiveness of an organization's cybersecurity program and identify gaps that need to be addressed.
Finally, the Framework can be used to benchmark an organization's cybersecurity program against others in the same industry. NIST is an internationally recognized and accepted framework in the cybersecurity community. Following this procedure ensures that your organization builds the most dependable foundation for its cybersecurity program.
While NIST 2.0 provides a wealth of resources to facilitate the implementation process, including quick-start guides, implementation examples, and detailed guidance materials, our team has some key tips to help kickstart your journey:
To effectively integrate the NIST 2.0 standards into your enterprise, consider the following tips:
Conduct a thorough gap analysis of your current cybersecurity framework against the updated NIST guidelines. Identify areas where your organization's practices align with the new standards and areas that require improvement or adjustment. This analysis will serve as the foundation for developing a roadmap towards compliance with NIST 2.0.
Obtain a comprehensive maturity score and target security posture assessment for your organization by leveraging future reports. These reports provide valuable insights into where your organization stands in terms of cybersecurity maturity and what steps are necessary to achieve the desired level of security posture outlined in the NIST 2.0 framework.
The Framework is voluntary and provides a flexible approach that can be tailored to the specific needs of any organization. It is not prescriptive, which means that organizations can choose the most appropriate controls for their particular circumstances. The Framework is also designed to be compatible with other security control frameworks, such as ISO 27001 and the Critical Infrastructure Protection (CIP) standards. When used correctly, it can help organizations of all sizes to develop a robust risk management strategy that takes into account their specific needs and priorities. Utilizing this framework can offer organizations a clear path forward for improving their cybersecurity posture and protecting their critical infrastructure. Threat Intelligence’s Evolve platform has security capabilities for each of the six pillars of the Framework - ranging from Automated Penetration Testing, Extended Detection and Response, Automated Incident Response to Automated Cyber Threat Intelligence, Leaked Password Monitoring, GRC Services and Supply Chain Monitoring.
Contact us if you would like to know more about how we can help you implement the NIST framework in your organization.
Related Content