SpiderX is a newly emerged ransomware group identified as the successor to the notorious Diablo group. This new cyber gang is gaining prominence due to its sophisticated techniques, advanced encryption methods, and aggressive tactics. This report delves into the technical aspects, attack vectors, indicators of compromise (IOCs), and MITRE ATT&CK framework mapping related to SpiderX.
SpiderX was announced by someone using the monocle ‘phant0m’ on a dark web cyber crime forum. The announcement claims the ransomware is written in C++, has very small payloads and can work in an ‘offline’ encryption mode
Technical Analysis
Encryption Methodology:
- ChaCha20-256 Encryption: SpiderX employs the ChaCha20-256 encryption algorithm, known for its speed and security, to encrypt files on the targeted systems. This algorithm ensures that the encryption process is both efficient and secure, making decryption without the key virtually impossible. Spider X also has the capability to encrypt external partitions such as USB drives and other flash storage devices.
Offline Capabilities:
- Local Encryption: Unlike many ransomware strains that rely on constant communication with command and control (C2) servers, SpiderX can perform encryption activities offline. This capability reduces its network footprint and makes it harder to detect through network traffic analysis.
Data Exfiltration:
- Information Stealer: SpiderX includes a built-in information stealer that exfiltrates sensitive data to external servers, specifically utilising the Mega cloud storage service (MegaNz). This dual-threat approach not only encrypts files but also poses a risk of data breaches.
Targeted Systems:
- Windows OS: SpiderX primarily targets systems running Windows OS, leveraging known vulnerabilities and user behaviours specific to this operating system.
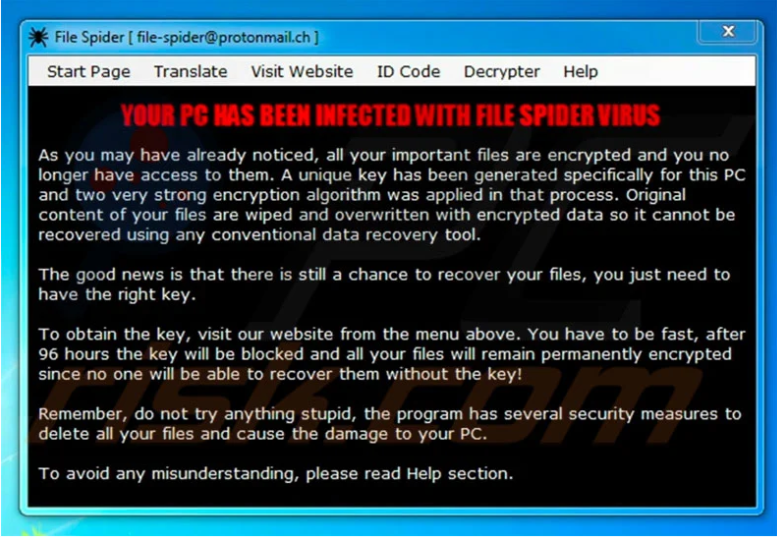
Screenshot of SpiderX’s Ransom Note on a Windows Machine
Attack Vectors
Initial Access:
- Phishing Emails: SpiderX commonly uses phishing emails to gain initial access to victim systems. These emails often contain malicious attachments or links that deploy the malware upon opening.
- Exploiting Vulnerabilities: The group exploits vulnerabilities in public-facing applications and services to gain unauthorised access.
Lateral Movement:
- PsExec and SystemBC: Once inside a network, SpiderX has been seen to use tools like PsExec and SystemBC to move laterally. PsExec is a legitimate Windows tool for executing processes on remote systems, while SystemBC is a proxy tool that facilitates communication with the C2 servers. Hower it is noted that SpiderX does not require a C2 connection.
Persistence:
- Remote Management Tools: SpiderX establishes persistence using Remote Monitoring and Management (RMM) tools, which allow them to maintain access over extended periods.
- Cobalt Strike: This advanced penetration testing tool is repurposed by SpiderX for maintaining persistent control over compromised networks.
Indicators of Compromise (IOCs)
File Extensions:
- .spx Extension: Files encrypted by SpiderX are typically appended with the .spx extension, indicating successful encryption.
C2 Communication:
- Tor Network: SpiderX uses the Tor network for C2 communications, enhancing its anonymity and making it harder to trace back to its operators.
Phishing Indicators:
- Aliases and Email Patterns: Commonly used aliases in phishing campaigns include names like "Jenny Brown." Emails are often crafted to appear legitimate and may impersonate trusted entities.
Malware Signatures:
- Hash Values: No hash values are available yet.
Initial Access (TA0001):
- Phishing: Use of spear-phishing emails to deliver malware payloads.
- Exploit Public-Facing Application: Leveraging vulnerabilities in web applications and services to gain entry.
Execution (TA0002):
- PowerShell: Utilises PowerShell scripts for executing commands and deploying payloads.
- Command and Scripting Interpreter: Executes commands and scripts on the target system.
Persistence (TA0003):
- Create Account: Creates new user accounts for maintaining access.
- Valid Accounts: Uses stolen or created accounts for persistent access.
Privilege Escalation (TA0004):
- Exploitation for Privilege Escalation: Exploits software vulnerabilities to gain higher privileges.
Defence Evasion (TA0005):
- Obfuscated Files or Information:
Uses obfuscation techniques to hide malicious code.
- Masquerading:
Disguises malicious activities as legitimate processes or services.
Collection (TA0009):
- Data from Local System: Collects sensitive data from local drives and directories.
Exfiltration (TA0010):
- Exfiltration Over C2 Channel:
Sends collected data to remote servers via the C2 channel.
MITRE ATT&CK Framework Mapping
Impact (TA0040):
- Data Encrypted for Impact:
Encrypts data to disrupt operations and extort ransom payments.
Mitigation Strategies
Patch Management:
- Regular Updates:
Ensure all software and systems are regularly updated and patched to mitigate known vulnerabilities.
Employee Training:
- Phishing Awareness:
Conduct regular training sessions to educate employees about phishing and social engineering tactics.
Network Segmentation:
- Limit Lateral Movement:
Implement network segmentation to isolate critical systems and limit the spread of malware.
Incident Response Plan:
- Preparation and Drills:
Develop and routinely update an incident response plan, including regular drills to ensure readiness.
Multi-Factor Authentication (MFA):
- Enhanced Security: Enable MFA for all critical systems and accounts to add an extra layer of security.
Conclusion
SpiderX represents a significant threat in the ransomware landscape due to its advanced techniques, robust encryption, and dual-threat approach of data encryption and exfiltration. Organisations must adopt a proactive stance, employing comprehensive security measures and maintaining vigilance to defend against this evolving threat.
Contact us today for a personalised consultation to discover how the
Evolve suite of products can meet your specific security needs. Our team will work with you to assess your current security posture, identify potential vulnerabilities, and tailor a solution that maximises protection and efficiency.
Schedule a consultation with one of our experts today!