Vulnerability management forms the foundation of any good security strategy because it shows you where your assets are most at risk. If you're researching vulnerability management solutions, you probably know that there are plenty of vendors out there and it's hard to find one that can do it all. It's even harder to find a vendor that can do it all well.
Tenable has been one of the most popular solutions in this space for years, leading the way with their Nessus vulnerability scanner and other exposure management solutions. In this blog post, we're introducing you to Evolve, a fully automated platform for vulnerability management and much more. We're going to compare the vulnerability management capabilities of Evolve with Tenable to help you make an informed decision about your future vendor.
Comparing Vulnerability Management Capabilities: Tenable vs Evolve
Understanding Tenable's Offerings
Tenable has four main offerings for vulnerability management: Nessus, Tenableio, Tenable Security Centre, and Tenbale Attack Surface Management (ASM).
Nessus is the flagship product, which is a vulnerability scanner. Tenable.IO is a cloud-based vulnerability management platform that lets you manage vulnerabilities from multiple scanners and remotely using agents. It also lets you add additional modules for web scanning, container security and others. And Tenable Security Centre is the on-premise version of Tenable.IO.
The difference between a vulnerability management platform and a vulnerability scanner is that the platform can be used to track your assets, create workflows, dashboards, and reports. While the scanner will perform a scan of your network and show you the vulnerabilities.
Why Choose Penetration Testing Over Vulnerability Scanning? (And Introducing EvolvePT)
Maybe you use a vulnerability scanner at present and it's working great for you. Why would you want to take the trouble of moving to a different approach?
There's no doubt that vulnerability scans can be useful tools in a security program. They can help you identify known vulnerabilities in your systems, prioritize which ones to fix first, and track your progress over time. And while this is a critical step in securing your infrastructure, after a point there's not much more you can do with a vulnerability scanner. A vulnerability scanner will tell you what holes are in your systems, and how to fix them. But a vulnerability scanner can't tell you who might be trying to exploit your organization's data, how they might be trying to do it, what vulnerabilities they're going to target, and what happens when they do.
Moreover, when conducting a vulnerability assessment, it's important to consider not just individual systems or applications, but also how they are interconnected and how vulnerabilities in one area can impact other parts of your infrastructure.
For example, a vulnerability in an internet-facing web application may not be immediately obvious, but when combined with a weak authentication mechanism on an internal system, it can provide an attacker with a pathway to access sensitive data. By conducting a comprehensive assessment that looks at all aspects of your infrastructure, you can identify these interconnections and understand how vulnerabilities in one area can impact other parts of your environment.
A vulnerability scan will also not be able to chain multiple vulnerabilities together to create a more powerful attack. However, these tests are critical to understand the true impact a breach can have on your business.
A pen test on the other hand, identifies holes in your systems, wants to understand how it could be or is being abused, and if it can be turned into a larger attack.
When compared to a vulnerability scan, a penetration test can offer 3 key benefits:
- Visibility: A pen test gives you a much deeper understanding of your environment and how it can be exploited by an attacker. While a vulnerability scan can only identify known vulnerabilities, a pen test simulates a real-world attack and tries to exploit any weaknesses that it finds, including those that may not be known to you or your security team. This provides you with a much more comprehensive view of your security posture and where you need to focus your efforts.
- Context: Penetration testing also provides valuable context that can help you better understand the risks to your business. Rather than just providing a list of vulnerabilities, a pen test shows you how an attacker could actually leverage those vulnerabilities to gain access to your systems or data. This helps you prioritize which vulnerabilities to fix first based on the real-world impact they could have on your organization.
- Real-world risk approach: Lastly, a pen test takes a risk-based approach to security testing. Instead of just focusing on technical vulnerabilities, a pen test also considers the people, processes, and physical security measures that could be exploited by an attacker. This provides a more holistic view of your security posture and helps you identify and address any weaknesses that could be exploited by an attacker in the real world.
EvolvePT is the automated penetration testing solution by Threat Intelligence. provides comprehensive coverage and detailed reporting to help organizations identify vulnerabilities and improve their security posture. Learn more about EvolvePT's advanced scanning and testing capabilities in the following sections.
The Importance of Comprehensive Coverage
EvolvePT - Extensive Coverage for Your Vulnerability Management Needs
A typical EvolvePT pen test includes the following 5 phases:
- Internet Reconnaissance - During this phase, we perform a deep dive into your network to find as many weak links as possible - covering employees, applications, IP addresses, DNS servers, darknet data, leaked credentials, malware infections, and more.
- Fingerprint and Scanning - This phase is performed to identify and scan all open ports and services on the target system, and to find any potential vulnerabilities.
- Attack and Exploitation - During this phase, the vulnerabilities are tested for exploitability by using exploits to break into the system. This allows for a realistic and accurate assessment of the risk posed by each vulnerability.
- Post-Exploitation and Lateral Movement - Once vulnerabilities have been successfully exploited, EvolvePT also offers deep coverage in its post-exploitation phase, which involves exploring the target system further to gain additional access and extract sensitive data. This can help identify additional vulnerabilities and weaknesses that may have been missed during earlier phases of the penetration test.
- Reporting - The final phase is the reporting phase, which is where the results are presented to the client.
This 5-stage process covers every possible attack scenario - from organization reconnaissance, man-in-the-middle attacks, automated exploitation, privilege escalation, and lateral movement, both in the cloud and across your organization’s security zones. It goes much further than a typical vulnerability scanner, which typically only covers the Fingerprint and Scanning phase, and may include a bit of the Exploitation phase.
Here's how this process compares to a traditional vulnerability scan:
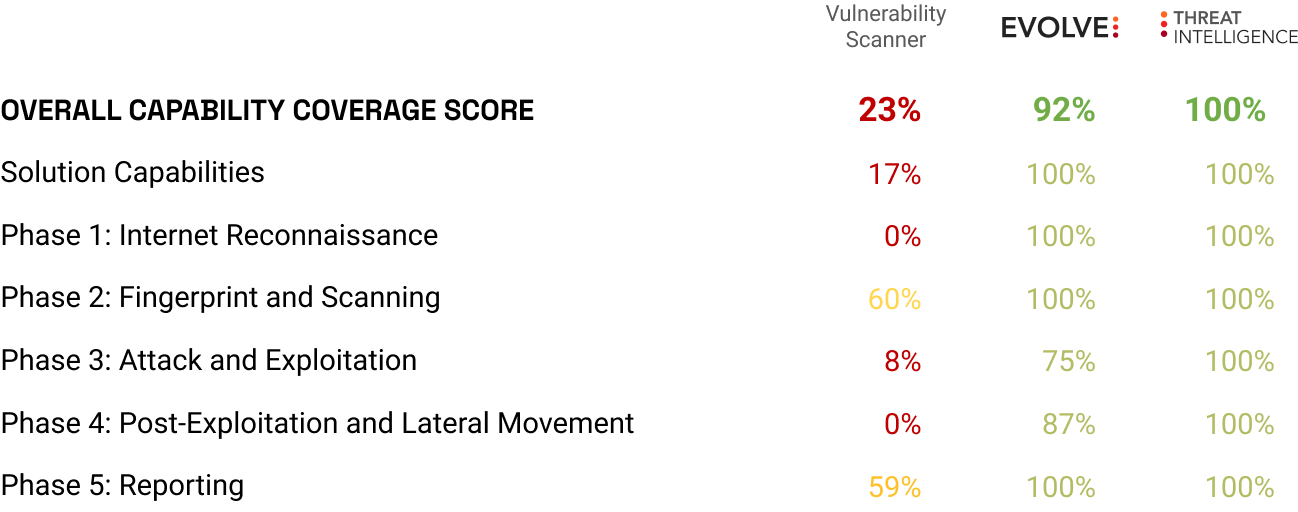
That's 70% more coverage than a traditional scan. For the full details and capabilities of EvolvePT, check out the report -
Vulnerability Scan vs Penetration Testing.
Why Reports Matter
Vulnerability scanning without an actionable report is as good as not scanning at all. Because if you don't know how to fix the vulnerabilities you've discovered, you're right back to where you started.
While Tenable's reports are generally well-regarded for their depth and detail, some users have reported certain drawbacks or limitations of the reports:
Complexity: Tenable reports can be quite complex and technical, which can make it difficult for non-technical stakeholders to understand the information presented.- Customization: While Tenable reports are highly configurable, some users have reported that it can be time-consuming to customize reports to their specific needs.
- False positives: Tenable reports may sometimes include false positives, which can lead to wasted time and resources if security teams investigate these issues unnecessarily.
- Limited context: Tenable reports may not always provide the context needed to understand the full impact of a vulnerability or security issue, which can make it difficult to prioritize remediation efforts effectively.
An EvolvePT report provides the right level of detail and clarity so your team knows exactly what to do. Check out how Evolve's reports address the following drawbacks:
Reports for Everyone
Technical details about vulnerability types and exploits may not always be understood by people outside of the security team. This is why it's essential to clearly communicate the severity of vulnerabilities in a way that non-technical stakeholders can understand. EvolvePT's reports provide a detailed Executive Summary with a separate section for executives and board members to understand where their organization stands in terms of security.
The Executive Summary is a high-level overview of the current state of your security posture - what are the areas you can improve and what are the next steps.
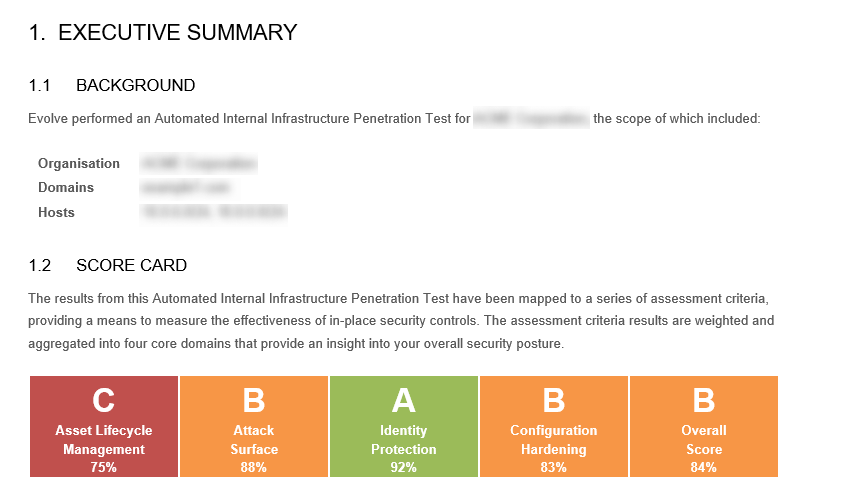
See The Big Picture - Vulnerabilities with Context and Insights
With EvolvePT's reports, you can get a detailed view of your vulnerabilities and their risk level, with a breakdown of the impact of each one in the Findings section of our report. This includes the exploits available for each vulnerability, and prioritization by exploitability. In addition to network and software vulnerabilities, you also get a detailed view of email security vulnerabilities, leaked authentication credentials, malware infections, DNS security vulnerabilities, dark web and reputation data that has been identified, and non-production systems that have been exposed, lateral movement and more - all of which can give you the necessary context to understand the severity of each vulnerability. Covering all of these aspects of your environment lets you see how the vulnerabilities from different areas are interconnected and how vulnerabilities in one area can impact other parts of your infrastructure.
Don't Cry Wolf - Minimum False Positives for Maximum Security
Our reports have an entire section dedicated to evidence, so you can see which vulnerabilities can be exploited to actually break into your systems.
This section provides evidence of the exploitability of the vulnerabilities found in your environment. If our solution is able to breach your network by exploiting the vulnerabilities found, you can find the proof of the breach in this section.
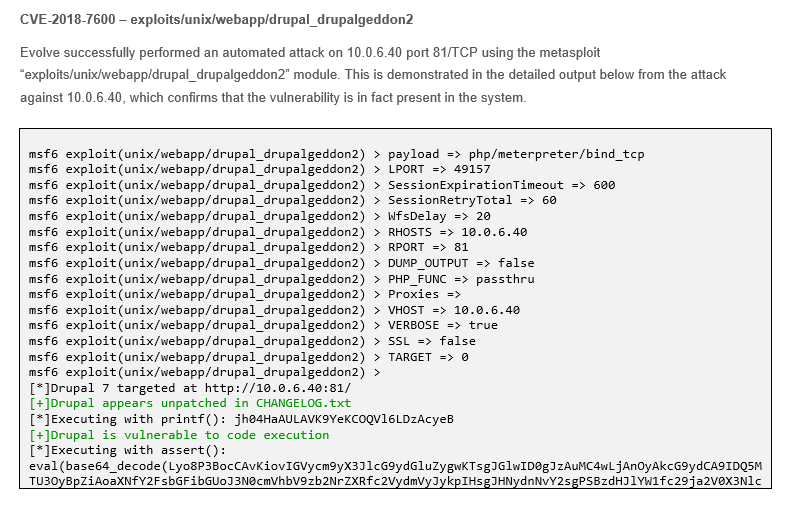
This unique feature of our reports is important because it validates the true positives, and thus helps you prioritize remediation efforts.
In the report, you'll also get a list of clear, and actionable next steps that you can take to remediate each vulnerability and further improve your security posture.
Cut Through The Noise: Customization for Clarity
If you're familiar with exploitability prioritization, you know that the only vulnerabilities that need immediate patching are the ones that are exploitable. With EvolvePT, you can get customized reports that let you see only the vulnerabilities that are exploitable so that you don't have to sift through a list of low-priority issues to find the ones that are truly important. Get the most critical risks at your fingertips, with a report that's customized to your exact needs.
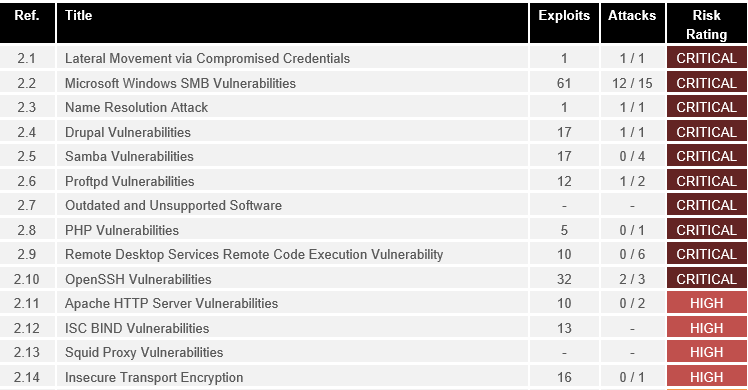
A Single Platform for All Your Vulnerability Management Needs
As we've covered in the beginning of this post, Tenable’s vulnerability management capabilities are spread across four different solutions - Nessus, Tenable.IO, Security Centre, and Attack Surface Management.
EvolvePT is an integration of the capabilities of all the above solutions into one solution, streamlining the vulnerability management process. And you also don't have to worry about managing multiple platforms, logins, and licensing agreements for each separate solution.
Security That Goes Beyond Vulnerability Management
The Benefits of Advanced Security Features
EvolvePT has a wide range of solutions to help meet your organization's unique needs. Leaked password monitoring can help you detect and respond quickly to compromised accounts, while supply chain monitoring helps ensure that your third-party vendors and suppliers don't introduce vulnerabilities into your environment. XDR capabilities provide a more holistic view of your security posture, while DNS sinkhole technology can prevent malicious connections to known bad domains. Threat intelligence and incident response are essential for rapid detection and response to cyber threats. Finally, web application scanning helps ensure that your applications are secure and compliant. With EvolvePT's advanced security features, you can achieve comprehensive coverage and robust protection for your organization.
A Platform That Does It All For You
Evolve isn't just a platform that does it all when it comes to cybersecurity, it's a platform that can do it all for you.
In addition to being a fully automated suite of solutions, Evolve can also be run as a fully managed service, minimizing human intervention and the potential for error. With a managed service, you also get access to the expertise of trained professionals who can manually review the results of automated scans, perform manual testing when required, and provide guidance and support when you need it.
Cybersecurity can be a time-consuming and resource-intensive task. By outsourcing your vulnerability management to a trusted provider like Evolve, you can free up your internal resources and focus on other important tasks, such as developing new products and services, building customer relationships, and growing your business.
Making the Right Choice: Which Solution is Right For You?
The ultimate goal of any security program must be threat and risk reduction rather than vulnerability reduction. While vulnerability scanning can provide a useful baseline of your security posture, it's unable to replicate the creativity and determination of a real attacker, leaving your organization exposed to sophisticated threats. Penetration testing, on the other hand, takes a more holistic approach by simulating a real-world attack, chaining issues, and demonstrating the true impact of a potential breach. By uncovering the critical vulnerabilities that pose the highest risk to your organization, a pen test can help you prioritize remediation efforts, reduce the likelihood of a successful attack, and achieve this goal.
In conclusion, when choosing the right security solution for your organization, it is essential to consider the features, capabilities, and levels of integration offered by each platform. EvolvePT and Tenable both provide robust security solutions, but EvolvePT stands out with its integrated approach and advanced features that go beyond traditional vulnerability management. Additionally, the option to use EvolvePT as a fully managed service minimizes the need for human intervention and reduces the potential for error. Ultimately, the choice between EvolvePT and Tenable will depend on your specific needs and preferences and the maturity of your security posture.
We hope that understanding their differences and strengths can help guide you to the most suitable solution for your organization.
We understand that the selection process can be daunting, and that we might not be the right solution for everyone. However, if you're interested in learning more about EvolvePT and how it can help with your vulnerability management needs, we'd love to hear from you. Feel free to reach out to us and
schedule a demo to see how our platform can help you achieve your goals.







