Two essential processes in the realm of cybersecurity, vulnerability management and patch management, play a crucial role in safeguarding systems and data. In this article, we will delve into the nuances of vulnerability management and patch management, exploring their differences, highlighting their importance, and providing insights into the role of security automation in enhancing these critical cybersecurity processes.
Vulnerability Management vs Patch Management
Vulnerability Management: Protecting Against the Unknown
Vulnerability management is a proactive approach to identifying, assessing, and prioritising vulnerabilities within an organization's IT infrastructure. It involves regularly scanning systems, networks, and applications to identify potential weaknesses that attackers could exploit. The primary goal of vulnerability management is to provide organisations with an in-depth understanding of their vulnerabilities, allowing them to allocate resources effectively and minimize risk.
The Vulnerability Management process consists of several key steps:
- Vulnerability Identification: This initial step involves scanning systems and networks to detect vulnerabilities and potential entry points for cyber threats. Through automated tools and manual assessments, organisations can uncover a range of weaknesses that may exist.
- Vulnerability Assessment: Once vulnerabilities are identified, they need to be assessed to understand their severity and potential impact. This step involves evaluating factors such as the likelihood of exploitation, potential consequences, and the affected systems or assets.
- Risk Prioritisation: After assessing vulnerabilities, organisations need to prioritise them based on their criticality. This involves assigning risk scores or ratings that take into account the severity of the vulnerability and the potential impact on the business.
- Remediation Planning: With a prioritised list of vulnerabilities, organisations can develop a remediation plan that outlines the necessary steps to address each vulnerability. This plan may include tasks such as applying patches, implementing configuration changes, or updating software versions.
- Patch Management: Patch Management focuses on the timely application of patches or software updates to address known vulnerabilities. It involves activities such as testing patches, scheduling deployments, and monitoring their effectiveness. Patch Management ensures that the necessary fixes are deployed promptly and effectively, bridging the gap between the identification of vulnerabilities and the implementation of effective solutions.
Patch management is basically the process of applying patches and updates to software and systems. These updates are applied to fix vulnerabilities, remove bugs, and improve functionality.
While
vulnerability management involves the identification, assessment, and prioritisation of vulnerabilities, patch management is a critical part of the process that focuses specifically on addressing known vulnerabilities through the timely application of patches or software updates.
Patch Management: Strengthening the Weakest Links
Patch management, focuses on the timely application of patches or software updates to address known vulnerabilities. Once vulnerabilities have been identified through vulnerability management processes, patch management ensures that the necessary fixes are deployed promptly. It involves activities such as testing patches, scheduling deployments, and monitoring their effectiveness. Patch management aims to bridge the gap between the identification of vulnerabilities and the implementation of effective solutions.
Here are the differences between vulnerability management and patch management at a glance:
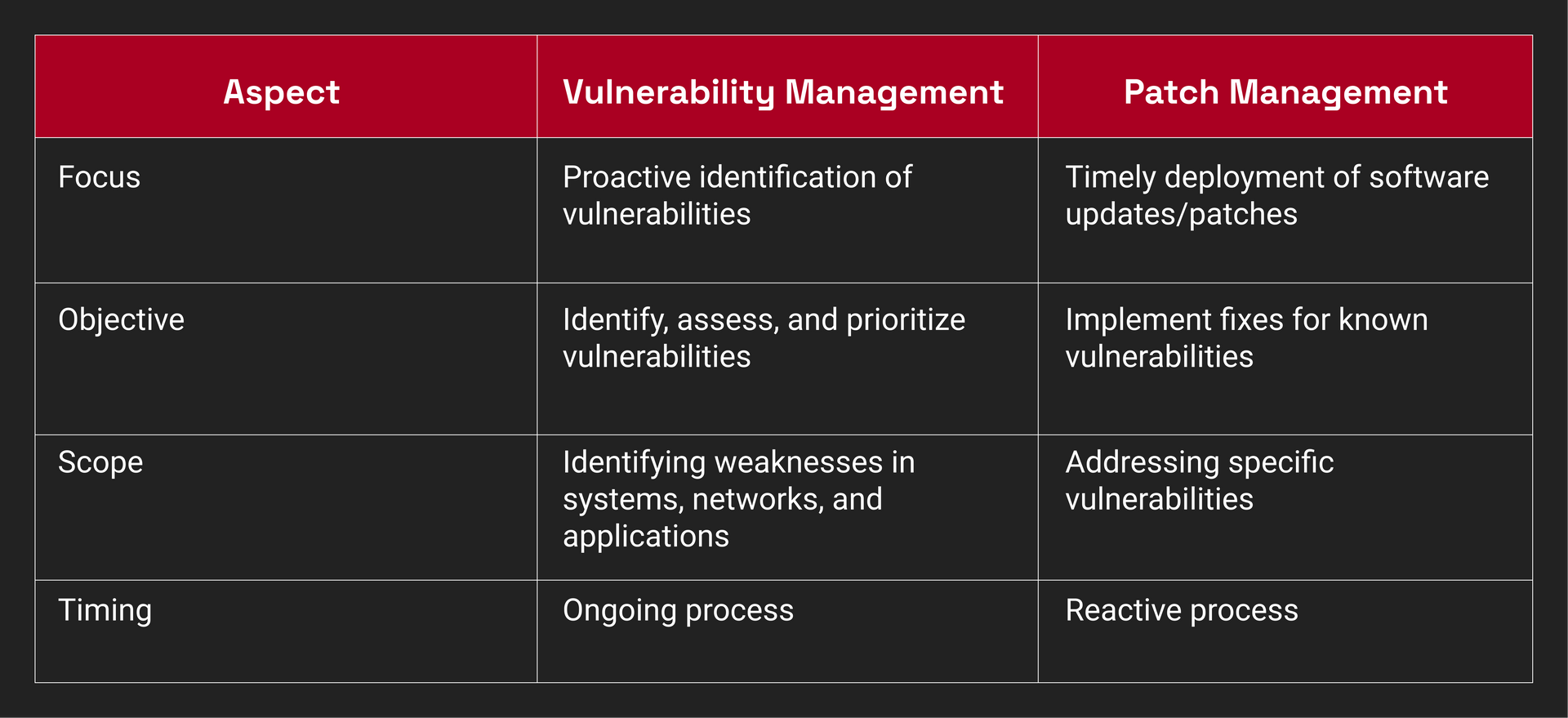
Differences between vulnerability management and patch management
The Significance of Vulnerability Management and Patch Management
Vulnerability Management: Staying Ahead of Threats
Vulnerability management is of paramount importance in the realm of cybersecurity. By proactively identifying vulnerabilities, organisations can stay one step ahead of potential threats. It enables businesses to assess their risk posture accurately, prioritise remediation efforts, and allocate resources efficiently. Vulnerability management empowers organisations to adopt a proactive security stance, enhancing their overall resilience against evolving cyber threats.
With a staggering
47% of security leaders reporting a backlog of vulnerable applications, it becomes clear that addressing vulnerabilities is an ongoing challenge that requires dedicated attention. The importance of effective vulnerability management becomes evident when considering the following points:
Firstly, organisations often struggle to keep up with the vulnerabilities they discover. With new vulnerabilities being discovered on a regular basis, it becomes a race against time to identify, assess, and remediate them before malicious actors can exploit them. Vulnerability management provides a systematic approach to prioritise and address vulnerabilities, ensuring that resources are allocated efficiently to mitigate the most critical risks.
Secondly, the issue lies not only in the volume of vulnerabilities but also in the proper triaging and patching of the right things. In a world of limited resources, it becomes essential to identify and prioritise vulnerabilities based on their potential impact and exploitability. Vulnerability management enables organisations to conduct thorough risk assessments and establish appropriate triage processes. By prioritising the vulnerabilities that pose the greatest threat, organisations can focus their efforts on patching the right things and reducing their exposure to potential attacks.
Moreover, vulnerability management aligns with compliance and regulatory requirements. Many industry standards and frameworks, such as the
Payment Card Industry Data Security Standard (PCI DSS) and the
General Data Protection Regulation (GDPR), emphasise the importance of vulnerability management as a fundamental security practice. Implementing robust vulnerability management processes can help organisations to comply with these requirements and demonstrate their commitment to data security.
Patch Management: Protecting against Exploits
Software vulnerabilities are inevitable, and without timely patching, organisations remain susceptible to exploitation. Patch management helps maintain system integrity, safeguarding sensitive data, and preserving the organization's reputation.
Patch management plays a crucial role in strengthening the weakest links in an organization's digital infrastructure. By swiftly applying patches, companies can reduce the attack surface and minimize the risk of successful exploitation.
Unpatched vulnerabilities have consistently been a leading cause of successful cyberattacks and continue to be an attractive target for attackers. In fact, unpatched vulnerabilities have been the root cause of some of the most high-profile cyberattacks in security history.
The infamous WannaCry ransomware attack in 2017, which affected thousands of organisations worldwide, exploited EternalBlue, a vulnerability for which a patch had been available long before the attack.
Another example is the Heartbleed vulnerability. A critical vulnerability in the open-source OpenSSL library that had gone completely undetected and unpatched for more than two years. These attacks succeeded solely because the underlying vulnerabilities were unpatched. And unfortunately, this trend continues today. In a concerning reality, a significant 60% of organisations faced the repercussions of breaches caused by neglecting to address well-known vulnerabilities through timely patching.
Patching vulnerabilities also extends beyond the realm of routine software and operating system updates. It involves the incremental reinforcement of your security posture, bolstering your defenses with each small yet meaningful improvement. By applying patches diligently, you forge a shield that fortifies your digital infrastructure, ensuring a stronger overall defense against cyber threats.
Enhancing Enterprise Security with Vulnerability Management and Patch Management
Vulnerability management and patch management may have different purposes but they are both necessary and in fact complementary for comprehensive security. Here's why:
Vulnerability Management: When Awareness is Paramount
Vulnerability management is crucial for organisations that prioritise proactive risk assessment and are focused on identifying and understanding potential vulnerabilities within their infrastructure. It is particularly beneficial for businesses that operate in high-risk sectors, handle sensitive data, or adhere to strict compliance regulations. Vulnerability management helps organisations gain visibility into their security posture and facilitates informed decision-making regarding resource allocation and risk mitigation strategies.
Patch Management: When Swift Remediation is Vital
Patch management becomes a priority for organisations with limited resources and a need for immediate vulnerability remediation. It is especially critical for organisations that rely on legacy systems or third-party software with known vulnerabilities. Patch management allows businesses to address vulnerabilities promptly, reduce the attack surface, and minimize the risk of exploitation. Enterprises operating in industries with stringent regulatory requirements often prioritise patch management to ensure compliance and data protection.
The Synergy of Vulnerability Management and Patch Management
While vulnerability management and patch management have distinct objectives, they work synergistically to enhance an organization's overall security posture. Vulnerability management helps identify and prioritise vulnerabilities, providing the foundation for effective patch management. By gaining visibility into vulnerabilities through vulnerability management processes, organisations can identify the appropriate patches required for remediation. Patch management, in turn, ensures the timely deployment of these patches, effectively reducing the attack surface and mitigating potential risks.
The Power of Security Automation
Streamlining Processes with Automation
Security automation plays a pivotal role in improving both vulnerability management and patch management. By leveraging automation tools, organisations can streamline vulnerability scanning, patch testing, deployment, and monitoring processes. Automation reduces manual effort, accelerates response times, and enhances overall efficiency. It enables organisations to scale their security operations, ensuring comprehensive coverage across complex infrastructures.
Continuous Monitoring and Remediation
Automated solutions offer continuous monitoring capabilities, ensuring that vulnerabilities are promptly identified and addressed. Automated patch management tools can detect missing patches, schedule deployments, and validate successful installations. Through automation, organisations can establish proactive security measures, reducing the window of opportunity for potential attackers.
Conclusion
After uncovering the differences and significance of vulnerability and patch management, it is evident that these distinct yet interdependent processes hold the key to robust cybersecurity. While vulnerability management empowers organizations to unearth potential weaknesses within their digital infrastructure, patch management acts as the swift and effective remedy, sealing vulnerabilities and fortifying the system's defenses.
With a comprehensive vulnerability management program, enterprises can proactively scan systems, networks, and applications, meticulously identifying vulnerabilities and assessing their potential impact. Armed with this knowledge, decision-makers can strategically allocate resources and prioritize risk mitigation efforts, staying one step ahead of potential threats.
But awareness alone is not enough. This is where patch management steps in, transforming vulnerability knowledge into tangible security enhancements. Through careful testing, scheduling, and deployment, patch management ensures that identified vulnerabilities are promptly addressed with the necessary software updates. This timely application of patches minimizes the attack surface, reducing the window of opportunity for malicious actors and safeguarding critical data.
As the digital landscape becomes increasingly complex and threats continue to evolve, organizations must adapt. Embracing automation is the key to effectively managing vulnerabilities and streamlining security operations. That's why we encourage you to explore Evolve Security Automation's cutting-edge solution: EvolvePT.
Our on-demand pen testing solution uses automation to elevate the vulnerability management process, reducing the time required to conduct and manage tests. With EvolvePT you can schedule tests anytime, anywhere, cover every possible attack scenario, and focus on patching the biggest threats first, leaving no room for vulnerabilities to go undetected or unaddressed. Schedule a demo today to learn more about how our solution can transform your security posture and fortify your digital environment.







